wolfSSL has partnered with Renesas to provide Renesas-based projects with SSL/TLS support via the wolfSSL embedded SSL/TLS library. The wolfSSL library supports several Renesas platforms (RX, RA, RZ, and Synergy) and has support for both Renesas CS+ and e2studio development environments. To make it easy to get started with wolfSSL, wolfSSL offers several example CS+ and e2studio projects which can be run on Starter Kits or Alpha Project boards, along with documentation on building wolfSSL for Renesas platforms. Several of the wolfSSL example CS+ and e2studio programs include SSL/TLS client/server example projects running on top of uITRON and TINET.
wolfSSL Product for Renesas
The following GitHub repository contains commercially licensed wolfSSL product code for use on specified Renesas platforms. This repository code is only properly licensed when following the license terms in the LICENSE file included in the repository. Reference the included README.md in the repository for the most up to date information on supported Renesas platforms, hardware security support, driver support, and more:
https://github.com/wolfssl/Renesas
Table of Contents:
Building wolfSSL with CS+
Renesas CS+ (formerly CubeSuite+) integrated development environment provides simplicity, security and ease of use in developing software through iterative cycles of editing, building, and debugging. In order to build the wolfSSL library, CS+ IDE project files have been included in the wolfSSL package, specifically in the <wolfSSL_root>/wolfSSL/IDE/Renesas/cs+/Projects directory.
-
- Compile wolfSSL library
- Open CS+ IDE project file at <wolfSSL_root>/IDE/Renesas/cs+/Projects/wolfssl_lib/wolfssl_lib.mtjp and compile
- Compile wolfCrypt test application
- Compile wolfSSL library
For getting BSP files:
-
-
- Create “bsp” directory under “Projects” directory
- Create “DUMMY” project under “bsp” with your MPU name property
- Close “DUMMY” project
-
Compile "test" project
-
- Open CS+ IDE project file at <wolfSSL_root>/IDE/Renesas/cs+/Projects/test/test.mtpj
- Change MPU name property of the project to match it to yours.
- Uncomment “Use SIM I/O” lines in “bsp/resetprg.c”
- Set heap size in “bsp/sbrk.h”
- Set stack size in “bsp/stackst.h”
- Start compile “test”
- Run the wolfCrypt cryptography test
Building wolfSSL with e2studio
Renesas e2studio is a development environment based on the popular Eclipse CDT (C/C++ Development Tooling), which includes build (editor, compiler and linker control), as well as debug interfaces. In order to build the wolfSSL library under the e2studio platform,e2studio projectfiles have been included in the wolfSSL package, under the <wolfSSL_root>/wolfSSL/IDE/Renesas/e2studio/Projects directory.
Steps to build wolfSSL library and wolfCrypt test application:
-
- Compile wolfSSL library
- Open e2 studio project file at /IDE/Renesas/e2studio/Projects/wolfssl/ directory and compile
- Compile wolfCrypt test application
- Compile wolfSSL library
Get missing files:
-
-
- Create “DUMMY” project
- Copy generated directory of DUMMY project under src directory of test project
-
Compile “test” project
-
- Open wolfCrypt test project file at < /IDE/Renesas/e2studio/Projects/test/ directory
- Uncomment “Use SIM I/O” lines in “resetprg.c”
- Set heap size in “bsp/sbrk.h”
- Set stack size in “bsp/stackst.h”
- Copy lowlvl.src, lowlvl.c and lowlvl.h in sample project’s that can be found the following link: https://www.renesas.com/jp/ja/software/D3012028.html
- Start compile “test”
- Run the wolfCrypt cryptography test
Building Renesas RX Project uITRON and TINET Demo projects
SSL/TLS server/client example project with AlphaProject with Renesas RX family MPU is also available at <wolfSSL_root>/IDE/Renesas/cs+/Projects/t4_demo/ directory. These example program use TINET network layer API on uITRON. The TINET API is incompatible with BSD. Therefore, this is also a good demo example how wolfSSL can fit into a non-BSD API easily.
Steps to build demo application:
- Download software.
- Unzip AlphaProject firmware
- Unzip wolfSSL under the same directory
- Set up wolfSSL
- Create the wolfSSL library as “Building wolfSSL with CS+ support” mentioned.
- Open t4_demo.mtpj at
IDE/Renesas/CS+/t4_demo/ directory and compile. This creates demo program library. - Set up AlphaProject
- Please see the README included in the directory.
Example projects
The wolfSSL package ships with several example projects which developers can use to get going quickly with wolfSSL on CS+ and e2studio platforms. The following example projects can be found under <wolfssl_root>/IDE/Renesas/es+(or e2studio)/Projects:
- wolfCrypt cryptography test
This application tests the wolfCrypt cryptography modules. It is generally a good idea to run this first on an MPU after compiling wolfSSL in order to verify all underlying crypto is working correctly.
- t4_demo application with CS+
This application is assumed to be built with an Alpha Project board with Renesas RX family MPU and its default firmware or driver. It includes TINET TCP/IP compatible Renesas firmware, T4Tiny.
The application has a console so that you can see message on the console prompting command as follows: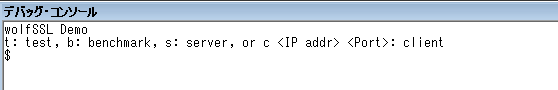
Command can be executed only once. You need to reset and restart MPU for following command:
t: wolfCrypt cryptography test
This application tests the wolfCrypt cryptography modules the same as above-mentioned test.
b: wolfCrypt benchmark test
This can be used on MPU to see cryptography algorithm benchmarks.
t: test, b: benchmark, s: server, or c : client $ b Start wolfCrypt Benchmark ------------------------------------------------------------------------------ wolfSSL version 4.0.0 ------------------------------------------------------------------------------ wolfCrypt Benchmark (block bytes 1024, min 1.0 sec each) RNG 775 KB took 1.031 seconds, 751.916 KB/s AES-128-CBC-enc 2 MB took 1.006 seconds, 1.505 MB/s AES-128-CBC-dec 1 MB took 1.010 seconds, 1.450 MB/s AES-192-CBC-enc 1 MB took 1.010 seconds, 1.378 MB/s AES-192-CBC-dec 1 MB took 1.011 seconds, 1.328 MB/s AES-256-CBC-enc 1 MB took 1.019 seconds, 1.270 MB/s AES-256-CBC-dec 1 MB took 1.014 seconds, 1.227 MB/s AES-128-GCM-enc 675 KB took 1.025 seconds, 658.858 KB/s AES-128-GCM-dec 675 KB took 1.026 seconds, 658.087 KB/s AES-192-GCM-enc 650 KB took 1.027 seconds, 633.220 KB/s AES-192-GCM-dec 650 KB took 1.028 seconds, 632.603 KB/s AES-256-GCM-enc 625 KB took 1.025 seconds, 609.697 KB/s AES-256-GCM-dec 625 KB took 1.026 seconds, 609.102 KB/s RABBIT 9 MB took 1.001 seconds, 8.534 MB/s 3DES 475 KB took 1.035 seconds, 458.893 KB/s MD5 13 MB took 1.001 seconds, 13.275 MB/s SHA 5 MB took 1.002 seconds, 4.778 MB/s SHA-256 2 MB took 1.006 seconds, 1.650 MB/s SHA-384 675 KB took 1.034 seconds, 653.057 KB/s SHA-512 675 KB took 1.034 seconds, 652.994 KB/s HMAC-MD5 13 MB took 1.001 seconds, 13.142 MB/s HMAC-SHA 5 MB took 1.004 seconds, 4.768 MB/s HMAC-SHA256 2 MB took 1.014 seconds, 1.638 MB/s HMAC-SHA384 650 KB took 1.010 seconds, 643.437 KB/s HMAC-SHA512 650 KB took 1.011 seconds, 643.182 KB/s RSA 2048 public 26 ops took 1.067 sec, avg 41.038 ms, 24.367 ops/sec RSA 2048 private 2 ops took 1.157 sec, avg 578.500 ms, 1.729 ops/sec DH 2048 key gen 6 ops took 1.049 sec, avg 174.883 ms, 5.718 ops/sec DH 2048 agree 6 ops took 1.191 sec, avg 198.433 ms, 5.039 ops/sec ECC 256 key gen 7 ops took 1.162 sec, avg 165.943 ms, 6.026 ops/sec ECDHE 256 agree 8 ops took 1.323 sec, avg 165.325 ms, 6.049 ops/sec ECDSA 256 sign 6 ops took 1.044 sec, avg 174.017 ms, 5.747 ops/sec ECDSA 256 verify 4 ops took 1.281 sec, avg 320.300 ms, 3.122 ops/sec CURVE 25519 key gen 5 ops took 1.137 sec, avg 227.300 ms, 4.399 ops/sec CURVE 25519 agree 6 ops took 1.366 sec, avg 227.583 ms, 4.394 ops/sec ED 25519 key gen 198 ops took 1.003 sec, avg 5.064 ms, 197.467 ops/sec ED 25519 sign 146 ops took 1.005 sec, avg 6.885 ms, 145.245 ops/sec ED 25519 verify 62 ops took 1.001 sec, avg 16.147 ms, 61.932 ops/sec Benchmark complete End wolfCrypt Benchmark
Note 1:
Test condition: BoardAP-RX71M-0A, MPU R5F571MLDDFC, CS+ v8.01.00,
Alpha Project example program v2.0
s: simple server accepting at port 50000
c: simple client. Specify IP address and port as c <IP Addr> <Port Num>
These applications are simple TLS client/server example programs using TINET TCP/IP connections. When testing the embedded client or server on MPU, it is recommended to test against one of the standard wolfSSL example applications running on a desktop machine.
[Client]
Desktop machine:
$ ./examples/server/server -b -d SSL version is TLSv1.2 SSL cipher suite is TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384 SSL curve name is SECP256R1 Client message: Hello Server
Board side:
wolfSSL Demo t: test, b: benchmark, s: server, or c <IP addr> <Port>: client $ c 192.168.1.202 11111 Start TLS Client(192.168.1.202, 11111) Received: I hear you fa shizzle! End TLS Client
[Server]
Board side:
wolfSSL Demo t: test, b: benchmark, s: server, or c <IP addr> <Port>: client $ s Start TLS Server Received: hello wolfssl! End TLS Server
Desktop machine:
$ ./examples/client/client -h 192.168.1.200 -p 50000 SSL version is TLSv1.2 SSL cipher suite is TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384 SSL curve name is SECP256R1 hello wolfssl!
Renesas TSIP Support
The wolfSSL embedded SSL/TLS library supports the Renesas Trusted Secure IP Driver (TSIP) and has been tested on the Renesas RX65N platform. Using the TSIP driver, wolfSSL can offload supported cryptographic and TLS operations to the underlying Renesas hardware for increased performance. For more information on wolfSSL TSIP support, please visit the following page:
About Renesas
Renesas Electronics Corporationdelivers trusted embedded design innovation with complete semiconductor solutions that enable billions of connected, intelligent devices to enhance the way people work and live. A global leader in microcontrollers, analog, power, and SoC products, Renesas provides comprehensive solutions for a broad range of automotive, industrial, home electronics, office automation, and information communication technology application that help shape a limitless future.

Renesas Electronics Corporation delivers trusted embedded design innovation with complete semiconductor solutions that enable billions of connected, intelligent devices to enhance the way people work and live. A global leader in microcontrollers, analog, power, and SoC products, Renesas provides comprehensive solutions for a broad range of automotive, industrial, home electronics, office automation, and information communication technology application that help shape a limitless future.
Reference
Alpha Project Co., Ltd: https://www.apnet.co.jp/eng/index.html
Renesas CS+: https://www.renesas.com/in/en/products/software-tools/tools/ide/csplus.html
Renesas e2studio: https://www.renesas.com/in/en/products/software-tools/tools/ide/e2studio.html