wolfSSL is thrilled to announce a significant milestone in browser security: the successful integration of wolfPKCS11 to provide FIPS 140-3 validated cryptography for the Mozilla Firefox browser. This is achieved by enabling wolfPKCS11 to serve as the backend cryptographic provider for Firefox’s Network Security Services (NSS) layer. This development represents a major step forward, bringing robust, federally-certified security to one of the world’s most popular web browsers.
This achievement builds directly upon a previously shared vision. Many may recall an earlier post, Why replace NSS with wolfSSL in Firefox?, which demonstrated the possibility of such an integration. It is with great excitement that this possibility is announced as a working reality. The core concept, replacing the underlying authentication implementations within NSS with the FIPS-validated capabilities of wolfCrypt via wolfPKCS11, has been brought to fruition.
For users and organizations operating in environments that require or prefer the assurances of FIPS 140-3 validated cryptography, this development is transformative. It means that Firefox can soon be leveraged with the formidable security backing of wolfSSL’s FIPS-certified cryptographic engine, wolfCrypt. While this advanced capability is fully functional and has been rigorously tested internally, it is important to note that it is not yet part of an official public release. Further announcements regarding public availability will be forthcoming. This progression from a proof-of-concept to a tangible, working solution underscores a commitment to not only innovate but also to deliver on complex technical challenges, reinforcing the reliability that is paramount in the security domain.
Why FIPS 140-3 in Your Browser is a Big Deal
Understanding the significance of this development begins with understanding FIPS 140-3. The Federal Information Processing Standard (FIPS) Publication 140-3 is a U.S. government standard developed by the National Institute of Standards and Technology (NIST). It specifies the security requirements for cryptographic modules, covering both hardware and software components that execute cryptographic functions. The primary role of FIPS 140-3 is to ensure that these cryptographic implementations meet stringent security benchmarks, thereby effectively protecting sensitive information. The gravity of this validation is starkly highlighted by NIST and the Canadian Centre for Cyber Security, which state that “non-validated cryptography is viewed as providing no protection to information—equivalent to plaintext”. This underscores the profound level of assurance that FIPS validation provides.
The mandate to use FIPS-validated cryptography is explicit for U.S. federal agencies when protecting sensitive information within their computer and telecommunication systems. This requirement frequently extends beyond direct government use, impacting contractors, organizations in regulated industries such as healthcare and finance, and entities pursuing critical certifications like the Cybersecurity Maturity Model Certification (CMMC). For other organizations, employing FIPS-validated cryptography serves as a clear indicator of a commitment to a high standard of security assurance.
Mozilla Firefox, along with other Mozilla products, relies on a set of libraries known as Network Security Services (NSS) for all its SSL/TLS, S/MIME, and other cryptographic operations. NSS is engineered to support cross-platform development and implements a comprehensive suite of internet security standards. A critical architectural feature of NSS is its utilization of the PKCS#11 standard. PKCS#11 is an API that governs communication with cryptographic tokens, which can be hardware accelerators, smart cards, or, as in this case, software-based modules often referred to as a “Software Security Device”. This adherence by NSS to the PKCS#11 standard is fundamental to the integration of wolfPKCS11. The combination of FIPS 140-3 defining what constitutes trusted cryptography and PKCS#11 providing how that trusted cryptography can be interfaced is powerful. Without NSS’s support for this standardized interface, replacing its cryptographic engine would be an extraordinarily complex, if not impossible, endeavor. This successful integration demonstrates how adherence to open standards can foster innovation and interoperability, ultimately benefiting end-users by making high-assurance cryptography accessible in mainstream applications like Firefox, potentially elevating the baseline for general web security expectations.
The wolfSSL Solution: wolfPKCS11 Powering NSS with FIPS-Certified wolfCrypt
The key to this enhanced security for Firefox is wolfPKCS11. This is wolfSSL’s robust implementation of the PKCS#11 API. The wolfPKCS11 module functions as an essential interface, or bridge, enabling applications that are designed to use the PKCS#11 standard (such as NSS) to access and utilize the comprehensive suite of cryptographic algorithms available within wolfSSL’s core cryptographic engine, wolfCrypt.
The integration leverages the “magic” of the PKCS#11 standard, which facilitates a “drop-in” replacement mechanism. NSS, by design, uses the PKCS#11 API to communicate with its default cryptographic library, which is softokn-freebl. The wolfPKCS11 module has been engineered to serve as a binary drop-in replacement for this default software security device. This means that, through modifications to configuration files rather than extensive code changes to Firefox itself, NSS can be directed to utilize wolfPKCS11. Consequently, all cryptographic calls from NSS are re-routed through wolfPKCS11 to the wolfCrypt engine. This elegant modularity, made possible by the PKCS#11 standard, significantly reduces the complexity and effort typically associated with integrating a new cryptographic provider into an established application like Firefox. The existence of this well-defined standard is a direct enabler of this relatively seamless integration path.
The true cryptographic power behind this solution resides in wolfCrypt, wolfSSL’s FIPS 140-3 validated cryptographic engine. wolfSSL has a distinguished history of achieving FIPS certifications, and wolfCrypt stands as a testament to this commitment, having attained FIPS 140-3 validation (the wolfCrypt module was one of the first in the world to receive a FIPS 140–3 Validation Certificate). It is this validation that imbues the Firefox integration with its robust security backbone and its capability to meet stringent compliance requirements. Beyond its FIPS validation, wolfCrypt is renowned for its exceptional performance, minimal footprint optimized for embedded systems, and extensive support for a wide array of cryptographic algorithms.
Seeing is Believing: FIPS-Powered Browsing (And Yes, It’s Real!)
It is understandable that FIPS-grade cryptography seamlessly operating within Firefox might sound almost too good to be true. To demonstrate that this is far more than just theoretical, it was even tested with some, shall we say, critical internet operations.
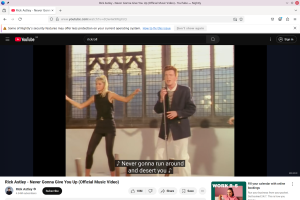
Caption: “Never Gonna Give Your Data Up: Firefox running with wolfSSL FIPS 140-3 security!”
Yes, that’s Firefox streaming a timeless classic. While the choice of content might be a playful rickroll, rest assured, the underlying FIPS 140-3 validated cryptography being provided by wolfPKCS11 and wolfCrypt is absolutely real and fully functional. If the system can handle real-world HTTPS traffic for streaming video (even this particular video), it is capable of many of today’s demanding browser use cases.
For those curious about how this appears “under the hood,” if one were to inspect Firefox’s security device manager, wolfPKCS11 would be visible as a loaded module.
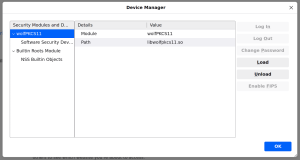
As mentioned, this powerful capability is confirmed and working seamlessly within our internal development environments. While it is not yet available in a public wolfPKCS11 release or as a standard component of Firefox distributions, work is progressing towards that goal. Keep an eye on the wolfSSL blog and official announcements for future updates.
Beyond the Browser: wolfSSL’s Commitment to Pervasive FIPS Security
The work to bring FIPS 140-3 validated cryptography to Firefox via NSS and wolfPKCS11 is not an isolated endeavor. It is a significant component of a much broader strategic initiative within wolfSSL: to make FIPS-certified cryptography readily and easily accessible across a diverse range of platforms and ecosystems.
This vision extends to enabling FIPS compliance across entire Linux distributions. There are ongoing efforts to integrate the wolfCrypt FIPS module with other critical system libraries, such as libgcrypt and GnuTLS. The ultimate objective is ambitious yet vital: “achieving FIPS 140-3 compliance across an entire Linux distribution”. Such an achievement would establish a unified, trusted cryptographic layer, thereby simplifying compliance efforts and significantly enhancing the security posture for countless applications and systems built upon these foundational open-source components. This strategy of embedding FIPS-validated technology deep within core operating system and application components positions wolfCrypt as a fundamental building block for secure systems, potentially establishing it as a de facto standard for FIPS cryptography in open-source environments.
Furthermore, the wolfPKCS11 module itself is designed with the future in mind. It is an evolving component, with enhancements such as upcoming support for the Leighton-Micali Signature (LMS) scheme planned. LMS is a stateful hash-based signature scheme, standardized in RFC 8554 and approved by NIST SP 800-208, notable for its quantum-resistant properties. This demonstrates a proactive stance towards emerging security threats. The engineering investment in wolfPKCS11 is therefore not limited to current FIPS standards; it is also paving a pathway towards post-quantum cryptography. This means that the very same integration mechanism being used to deliver FIPS 140-3 validated cryptography to Firefox today could potentially deliver post-quantum security in the future, thanks to the flexible and standards-compliant design of wolfPKCS11.
Conclusion: Secure Your Firefox Experience, Trust wolfSSL
To summarize this exciting development: wolfSSL has successfully made FIPS 140-3 validated cryptography a practical reality for the Firefox browser. This has been achieved by integrating the wolfPKCS11 module with Firefox’s Network Security Services (NSS), thereby allowing Firefox to leverage the proven strength of the wolfCrypt FIPS-certified engine.
The benefits of this integration are manifold. It provides access to high-assurance, FIPS-validated security within one of the world’s leading web browsers. For organizations with FIPS compliance mandates, it offers a significantly simplified path to meeting those requirements for browser-based activities. All of this is delivered with the robust, performant, and resource-efficient cryptography that wolfSSL is known for.
This advancement is another clear testament to wolfSSL’s leadership in embedded security, cryptography, and FIPS validation. The commitment at wolfSSL is to provide cutting-edge, reliable security solutions that meet the evolving challenges of the digital world. This successful integration reinforces that commitment and highlights the dedication to enhancing security for users everywhere.
Get in Touch / Download wolfSSL
Stay tuned to our blog for updates on the public availability of this feature!
If you have questions about any of the above, or how wolfSSL can help secure your applications, please contact us at facts@wolfSSL.com or call us at +1 425 245 8247.
Download wolfSSL Now



