TPM vs HSM, what’s the difference? Check out this blog post for more detailed.
In a nutshell, TPMs are typically a dedicated chip included along side a main (host) processor and used for securing a single consumer electronics device. HSMs are external devices that can be used across multiple devices and systems, offering advanced cryptographic operations and key management. For both of them, their main objective is to protect and store private key material. A TPM typically presents itself via the standardized TPM 2.0 API while an HSM presents itself via the standardized PKCS11 API.
If you think about it really, really carefully, the difference is just a matter of form factor, interfaces, and regulatory technicalities. So is it possible for a TPM to present itself as an HSM? The answer is most definitely YES! But how?
Here at wolfSSL we have our own PKCS11 provider library, wolfPKCS11, to leverage cryptographic hardware and keystores on various systems. A while ago, we added support for using TPM 2.0 modules via wolfTPM into wolfPKCS11. We believe that this functionality is particularly useful for users that have coded to the PKCS11 standard, but need to switch to a TPM or fTPM; there are many technical and business reasons to do so.
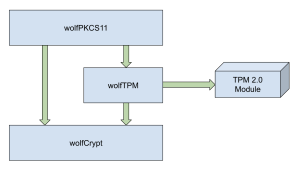
With that in mind, if you have been using an HSM and want to simplify to simply using a TPM with little to no code changes in your application, let us help you with that. Reach out to us to find out how your specific situation would work!
If you have questions about any of the above, please contact us at facts@wolfssl.com or call us at +1 425 245 8247.
Download wolfSSL Now

