PRODUCTS
wolfSSL Support for Post-Quantum
wolfSSL, the world’s first cryptography provider supporting CNSA 2.0 compliance, leads in robust post-quantum cryptography solutions, including ML-KEM (Kyber) key encapsulation and ML-DSA (Dilithium) digital signatures. For more information on wolfSSL's Post-Quantum Cryptography solutions, contact us at facts@wolfSSL.com today!
Download wolfSSL and stay ahead of the quantum curve.
PQC FIPS Certification in process! Learn more
Highlights
- CNSA 2.0-compliant post-quantum algorithms like ML-KEM and ML-DSA, meeting FIPS 203 & 204 standards.
- Hash-based SLH-DSA, LMS, and XMSS signatures for both stateful and stateless options.
- Performance-optimized for x86_64 and ARM architectures, ideal for embedded systems with a small footprint and bare-metal support.
- Fully integrated in wolfCrypt, with (D)TLS 1.3 support for seamless PQC adoption.
- Available in wolfBoot, wolfMQTT, wolfSSH, curl, and Apache Web Server for flexible PQC support.
- Coming soon: PQC Algorithms in wolfTPM!
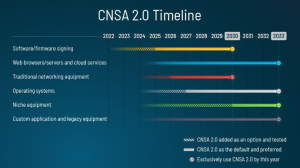
Algorithm Support in wolfCrypt
KEM (Key Encapsulation Mechanism)
Implementation of ML-KEM (Kyber) Parameter sets:
- ML-KEM-512
- ML-KEM-768
- ML-KEM-1024 (CNSA 2.0 compliant)
- Optimizations for x86_64 and ARM
General Signature Schemes
Implementation of ML-DSA (Dilthium) Parameter sets:
- ML-DSA-44
- ML-DSA-65
- ML-DSA-87 (CNSA 2.0 compliant)
- Optimizations for x86_64 and ARM
Stateless Hash-Based Signature Schemes
SPHINCS+ via integration with liboqs Parameter sets:
- SPHINCS+-SHAKE-128f-simple
- SPHINCS+-SHAKE-192f-simple
- SPHINCS+-SHAKE-256f-simple
- SPHINCS+-SHAKE-128s-simple
- SPHINCS+-SHAKE-192s-simple
- SPHINCS+-SHAKE-256s-simple
Stateful Hash-Based Signature Schemes
Implementation of LMS/HSS (CNSA 2.0 compliant)
- RFC 8554
Implementation of XMSS/XMSS^MT (CNSA 2.0 compliant)
- RFC 8391
Protocol Support
(D)TLS 1.3, MQTTv5, and MQTT-SN
Supported Groups Extension Codepoints
- ML_KEM_512
- ML_KEM_768
- ML_KEM_1024 (CNSA 2.0 compliant)
- P256_ML_KEM_512 (hybrid with FIPS 140-3)
- P384_ML_KEM_768 (hybrid with FIPS 140-3)
- P521_ML_KEM_1024 (hybrid with FIPS 140-3; CNSA 2.0 compliant)
- P256_ML_KEM_768 (hybrid with FIPS 140-3)
- P384_ML_KEM_1024 (hybrid with FIPS 140-3; CNSA 2.0 compliant)
- X25519_ML_KEM_768 (hybrid with FIPS 140-3)
Sigalgs Extension Codepoints
- ML_DSA_44
- ML_DSA_65
- ML_DSA_87 (CNSA 2.0 compliant)
- X9.146 CKS TLS 1.3 Extensions for signature algorithm negotiation
Symmetric Ciphers
- TLS_AES_128_GCM_SHA256 (FIPS 140-3 Compliant)
- TLS_AES_256_GCM_SHA384 (FIPS 140-3 and CNSA 2.0 Compliant)
X.509 2019 Edition (Chimera Certificates)
- Alternative Subject Public Key Extension
- Alternative Signature Algorithm Extension
- Alternative Signature Value Extension
SSHv2
- mlkem768nistp256-sha256 (hybrid with FIPS 140-3)
- mlkem1024nistp384-sha384
- mlkem768x25519-sha256
Post-Quantum Integrations against wolfSSL/wolfCrypt
- wolfMQTT
- wolfBoot (LMS/HSS, XMSS/XMSS^MT, ML-DSA and ECDSA hybrid,
ML-DSA) - wolfSSH
- wolfHSM
- curl Web Client
- Apache Web Server
- Lighttpd Web Server
- Nginx Web Server
- Stunnel
- STM32CubeIDE
Learn more about Post-Quantum Integrations in our blog post here and here.
wolfSSL Post-Quantum Products in Production
- ExpressVPN’s Lightway Protocol using (D)TLS 1.3 with Post-Quantum Algorithms Protecting Millions of Devices
Learn more!
Collaboration Projects
- NIST’s (National Institute of Standards and Technology) NCCoE (National Cybersecurity Center of Excellence) Migration to Post-Quantum Cryptography Project
- wolfSSL and Crypto4A interoperability between wolfBoot and QXEdget Using LMS demo project
- wolfSSL and AWS interoperability between wolfSSH and AWS Transfer Family using ML-KEM and ECDH hybrid scheme
Benchmarks
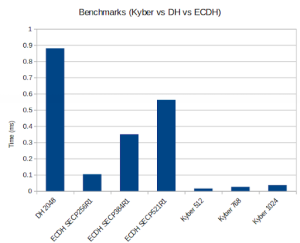
Post-Quantum Kyber (Linux)
Platform: 11th Gen Intel® Core™ i7-1185G7 @ 3.00GHz × 8
Benchmark:
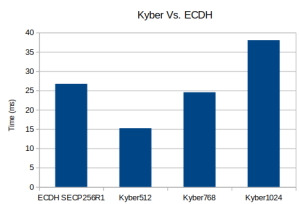
Post-Quantum Kyber Benchmarks (ARM Cortex-M4)
Platform: STM NUCLEO-F446ZE
Benchmark:
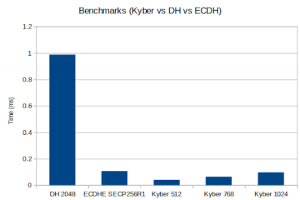
Post-Quantum Kyber Benchmarks (MacOS)
Platform: Apple MacBook Pro 18,3 with an Apple M1 Pro, 3.09 GHz processor
Benchmark:
Release Plan
- FIPS 140-3 PQC Certification in Progress
- ACVP and CMVP certification of our post-quantum algorithms
- Integrations against more open source projects to make them quantum-safe
- Add Curve25519 hybridized with ML-DSA in wolfSSL, wolfSSH and wolfMQTT
- Support for PKI artifact generation using post-quantum algorithms in wolfCLU
- Post-quantum algorithm support in wolfHSM, including LMS and XMSS
- LMS support in wolfSSL PKCS11 consumer
- LMS support in wolfPKCS11
- Expand supported post-quantum algorithms, including FrodoKEM, SLH-DSA, and HQC
- Monitor “post-quantum on-ramp for signatures” and implement the winners
- Bring mlkem1024nistp384-sha384 and mlkem768x25519-sha256 to wolfSSH
- Integrate wolfTPM with post-quantum enabled TPMs, including ML-KEM and ML-DSA support
- Post-quantum cryptography support in wolfProvider amd wolfPKCS#11
Resource
Documentation & examples
Post-Quantum Cryptography Video Series
Explore our full video series on Post-Quantum Cryptography in the YouTube playlist!

