
About Me
For this blog post, I’m going to do something a little different. This is a personal project, and as such, you should probably know a little about the person behind it. My name is Andrew Hutchings, I have an extensive engineering background, and in my spare time, I design new circuit boards for vintage computers.
I was part of the wolfSSL team at Embedded World 2025. This is a photo of the team there, I’m the one in the light-blue jeans.
I’m also wearing a badge here, which I designed, which is an entirely custom board using an RP2040 microcontroller and power management/battery management hardware. It uses a highly optimised OLED driver and graphics library firmware I wrote for it.
At Embedded World, we were showcasing various wolfSSL products running on stock development boards. It was here I had the thought “what if we had our own development board?”. In my hotel room, I got to work on planning and designing. There are some basic requirements I wanted to target:
- It had to have wolfSSL branding and draw attention.
- It had to have mikroBus sockets. Pretty much every expansion possible is available in the open mikroBus standard.
- It should be easy to use for people who are not as experienced in embedded development.
- It should have a Tag-Connect connector for the JTAG. This is just a personal thing, I use Tag-Connect everywhere.
I quickly settled on the STM32U585 for this board. It has a lot of flash and RAM, hardware crypto acceleration for AES and SHA-256, it is quite fast (Cortex-M33 at 160MHz) and relatively inexpensive. I’ve also developed ST based boards before. So, whilst I figured that I would end up doing boards with other manufacturer’s MCUs, this would be a lower barrier to a first version.
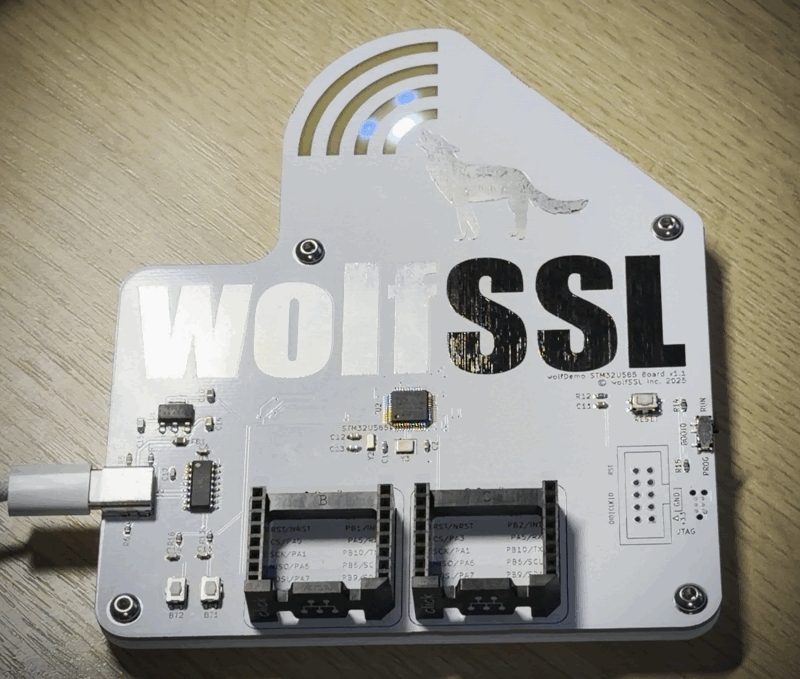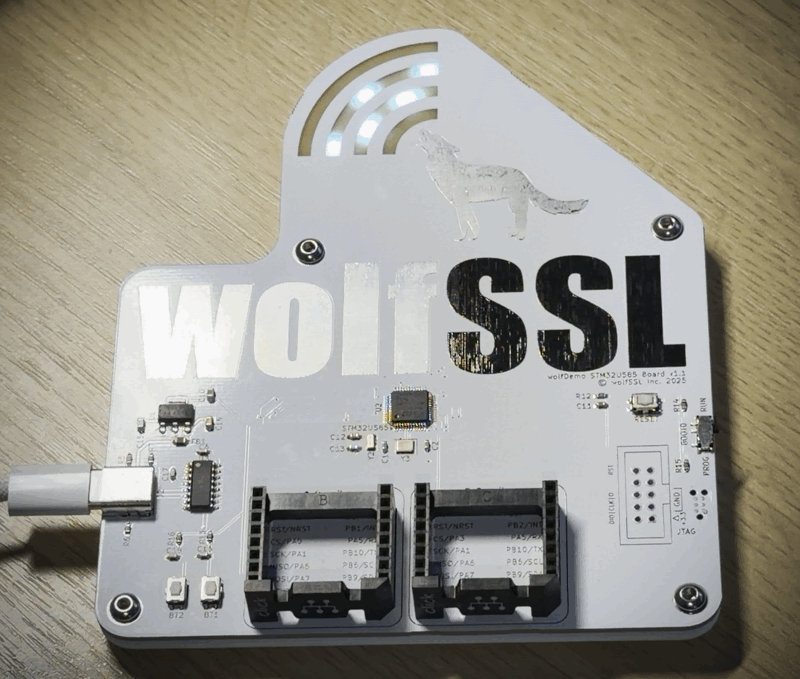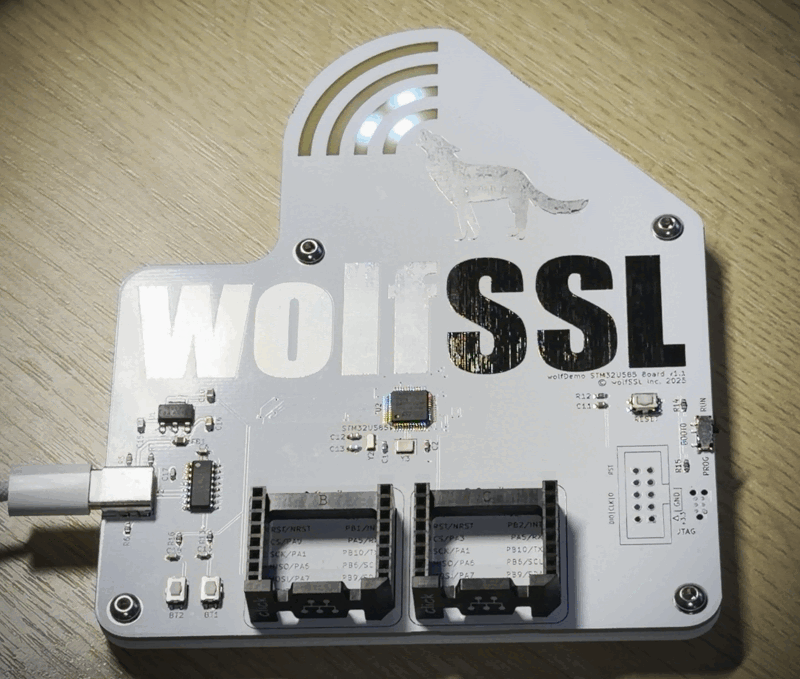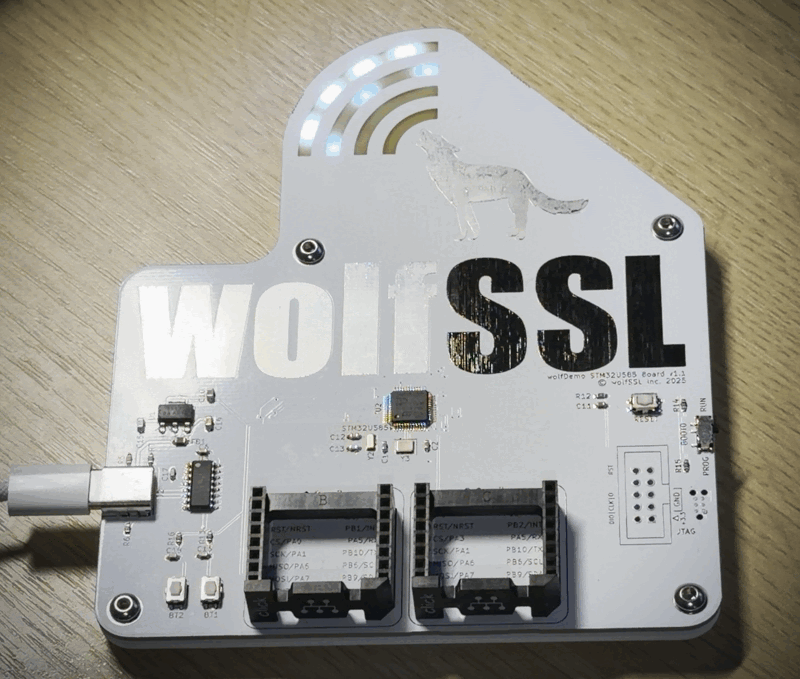
The wolfDemo Board

The final version of the board I think met all my requirements. I used various aspects of the PCB to make the wolfSSL logo and put four addressable cyan LED sections underneath the board to glow for the wolf’s bark, one section for each of the curved bars for the bark. You can see the third from the right bar glowing in the photo above. There are two mikroBus sockets, two input buttons, and a USB to UART for getting log data or flashing the board. It even has Tag-Connect for JTAG, as well as an option for a 10-pin ARM Cortex JTAG header.
In addition, I created a mikroBus click board for the ST33 TPM.
Better Demos
Now that we have a board, we need demos to run on it. We have the wolfCrypt benchmark, it is a great way to show how fast wolfCrypt runs on various platforms. But, at a casual glance in an expo environment, it isn’t the easiest to understand. So, I made some improvements…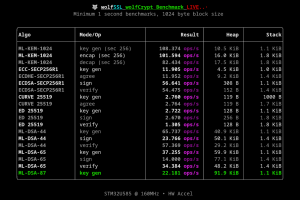
Behind the scenes, there is the regular wolfCrypt benchmark running underneath. Although there is a new feature I wrote to show the heap / stack usage for each algo. The front end you are seeing here is a Python script that listens on the USB serial port and processes the results in real-time, rendering it into the table. Also, for an added visual touch, as each log line is sent from the board, the wolf bark LED changes.
What’s Next!
This is not something we will be selling. I’m going to be making more boards in my spare time and sending them to the rest of the team. In fact, I’ve sent some already and have a batch ready to go. This way we can show demos on the board at more events. We have also made the design files and examples publicly available.
There will definitely be more demos. I showed the board for the first time at it-sa in Nuremberg, and partners have already approached us saying that they would like demos of their technology on it. With the mikroBus sockets, we can show wolfSSL’s products running whilst connected to hundreds of different hardware boards.
I will also be designing variants using MCUs from other companies, so that we can show that wolfSSL’s products are extremely versatile.
If you are coming to an event, and wolfSSL is there. Lookout for demos using the wolfDemo board!
If you have questions about any of the above, please contact us at facts@wolfssl.com or call us at +1 425 245 8247.
Download wolfSSL Now

