TLDR: wolfSSL can run over CAN Bus. This means wolfSSL can secure CAN Bus, which is typically insecure. As such, you can now authenticate over CAN Bus and encrypt over CAN Bus.
The CAN (Controller Area Network) bus is a common data bus used in vehicles for onboard microcontrollers to communicate to each other. Modern vehicles have dozens of microcontrollers inside them and the usage of this technology is only going to grow in road vehicles as newer safety standards come into effect. Vehicle computers are becoming rather powerful and there have already been instances in the media of these computers being remotely hacked. Security, therefore, will become an important part of CAN bus communication over the coming years.
Part of the downside of the CAN bus protocol is that it only supports a payload of up to 8 bytes per packet, so there are layers on top of this to add flow control and packet headers so that larger packets can be reliably sent. One of the most common of these is ISO-TP (ISO 15765-2), which is regularly used for things such as OBD-2 diagnostic messaging.
A great thing about ISO-TP is that it allows us to send packets of up to 4KB and a great thing about wolfSSL is that you can hook it into pretty much anything with a data send and receive function. We have therefore created an example of how to hook wolfSSL into ISO-TP and use this over a CAN bus. This example can be found at https://github.com/wolfSSL/wolfssl-examples/tree/master/can-bus. This is a simple echo client and server which will negotiate a TLS handshake and then send / receive encrypted messages. The Linux kernel has a built-in virtual CAN bus as documented in the README, but you can use a real CAN bus to try this on. For example, here is one I made earlier between my laptop and a Raspberry Pi 3A: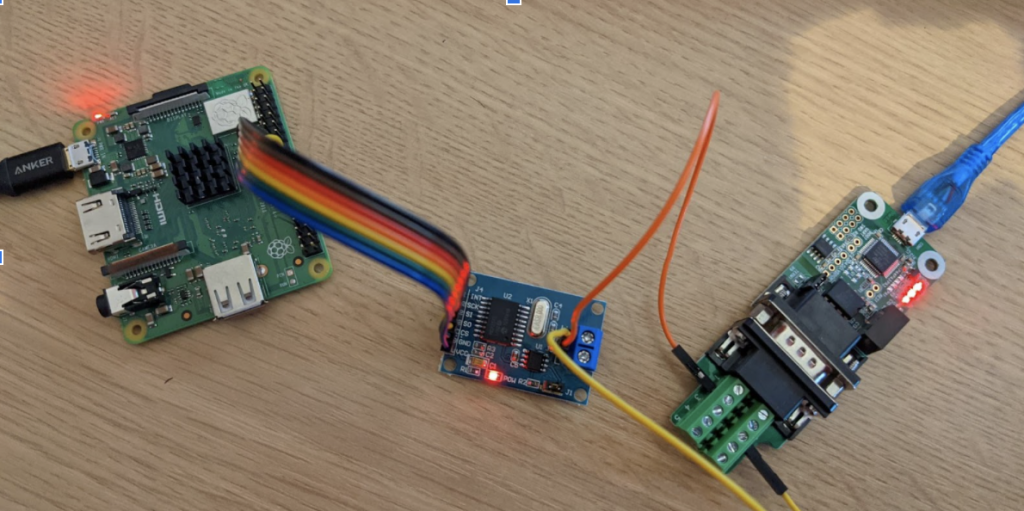
Using this setup the example works as below:
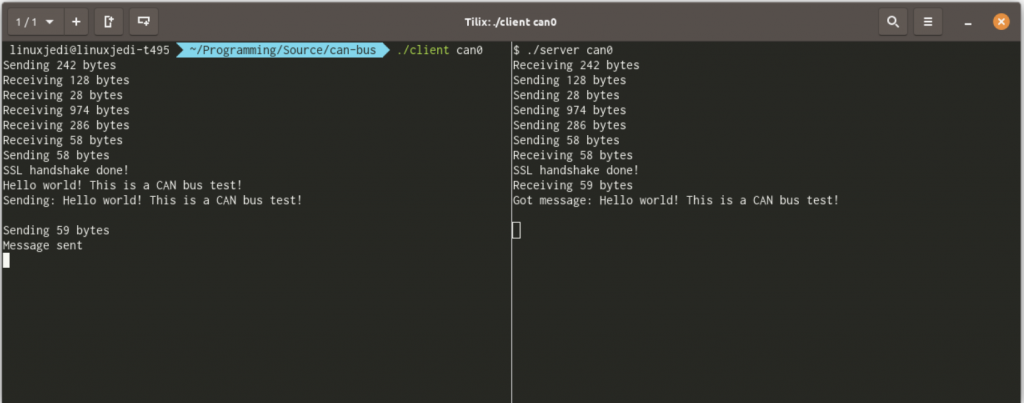
And that is it! The code is relatively simple to go through but feel free to contact us for more information. Look out for more CAN bus security tools from wolfSSL in the future.
Need more? Subscribe to our YouTube channel for access to wolfSSL webinars!
Love it? Star us on GitHub!
If you have any questions or run into any issues, contact us at facts@wolfssl.com, or call us at +1 425 245 8247.

