We often get questions from users of the wolfSSL embedded SSL/TLS library about which certs to load and why. So today we wanted to discuss the following topics:
- What is a cert chain as seen in a common browser?
- What is a public key, what is a private key?
- What is the chain of trust and why is it “trustworthy”?
- How does one know which certs to load into their application?
What is a cert chain as seen in a common browser?
When we go to a website like www.google.com we see a little green lock that shows it provides security. If we investigate a little further by clicking on that little green lock we might see something like this:
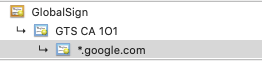
What does each of these items mean? What is “GlobalSign”, what is “GTS CA 101”, and what is “*.google.com”? Well let’s break it down:
- *.google.com (Bottom of the chain) – This is the certificate that has been issued for any domain ending in “google.com”.
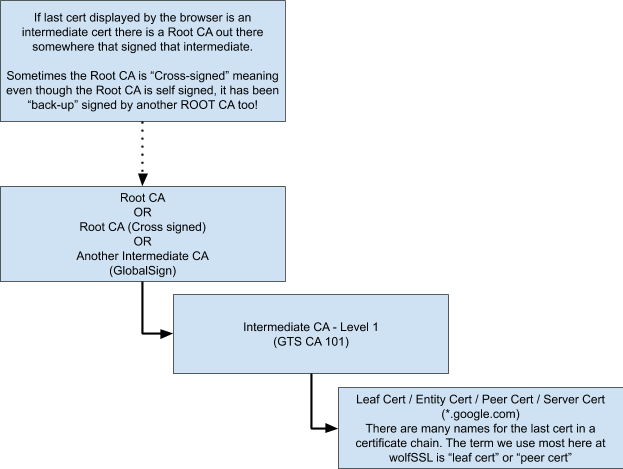
- GTS CA 101 (Second cert from the bottom) – This is an intermediate CA certificate (we’ll go more into why an intermediate is necessary in the chain of trust below)
- GlobalSign (The top level cert seen in the browser) – This can be any number of things, depending on the website you are connecting to, this might be another intermediate CA that signed the first intermediate CA. This might be a self-signed root certificate. This could also be a self-signed root CA that is cross-signed. (We’ll cover cross-signing below)
What is a public key, what is a private key?
Certificates contain public keys. Public keys are designed to be distributed. Anyone can have a copy of the public key and all certs contain a copy of the public key that is associated mathematically with their private key. Public keys can not be used to derive the private key. Think of a public key as `the Flour in a cooking recipe. You can have bleached white wheat flour (RSA), whole wheat flour (ECC), or maybe Cornmeal Flour (PSK). So we can tell what kind of flour we have great! But we can’t tell if the flour was used in a pancake, or a muffin, or bread, in other words we are given access to the flour (the public key) but we can’t derive what the private key is simply by knowing the type of flour that was used, the private key has other ingredients we don’t have access to so we can’t derive the private key from the public key. Traditionally public keys are used to “verify” things that have been signed by their corresponding private key. There are cases where a public key can also be used to sign and the private key used to verify that signature.
So why bother going into the details of the keys? Well let’s get back to certs:
The entity certificate (*.google.com) uses the private key it is associated with to sign and verify things during a TLS connection so a copy of that private key has to be present on every server using this cert. So why don’t we just trust this cert? The answer is it can not truly be trusted stand alone, since the private key associated with that certificate is too commonly distributed to be trustworthy all on it’s own. Imagine if just one of the thousands of Google servers became compromised somehow and someone was able to steal the private key for the cert that works on any Google server? Now that bad-actor could start making their own certs using the private key for *.google.com and standing up malicious servers like supertrustyserver.google.com and your browser would automatically trust it if said actor can get you to click on a link that leads to his server, you would just think you are on google.com but the bad actor might be logging everything you enter in the browser while you’re using his server or trying to get your browser to launch scripts in the background that do any manner of things etc. Not a good situation. So to avoid this kind of compromise a need to establish a “chain of trust” was deemed necessary in the early days of the Internet.
What is the chain of trust and why is it “trustworthy”?
With each certificate higher in the chain of trust, theoretically the private key for that cert is more difficult to obtain and the probability of that private key becoming compromised is reduced. The less likely a private key is to be stolen, the more trustworthy it becomes. Private keys associated with Root CA’s being theoretically impossible to steal with rigorous oversight and audit from both government and private sector entities. Private keys for Root CA’s are never supposed to come in contact with the Internet (strictly offline use) and are only accessed in a secure room by a select few individuals.
So the process for creating a chain of trust goes:
- CA_ROOT_PRIVATE_KEY created in a clean room on a disconnected computer. CA_ROOT_CERTIFICATE created with the private key and signed by the private key (self-signed certificate). Just the CA_ROOT_CERTIFICATE, not the private key, will later be transferred to a connected system from where it can be disseminated to all browser manufacturers for trusting (Chrome, Firefox, Explorer, Safari, Netscape, DuckDuckGo, … etc)).
- INTERMEDIATE_CA_PRIVATE_KEY created safely (probably a similar process to how the CA_ROOT_PRIVATE_KEY is created in step 1, INTERMEDIATE_CA_CERTIFICATE created FROM INTERMEDIATE_CA_PRIVATE_KEY and signed by CA_ROOT_PRIVATE_KEY.
- CA_ROOT_PRIVATE_KEY securly stored (subject to oversight) and lock it up never to be touched again except in the event the CA_ROOT_CERTIFICATE is about to expire and needs updated or a new intermediate CA needs to be signed after creation.
- Distribute the INTERMEDIATE_CA_PRIVATE_KEY for use by employees of the CA organization. This INTERMEDIATE_CA_PRIVATE_KEY is used only by employees of the CA organization at their work stations.
- Company like Google creates a LEAF_PRIVATE_KEY for their own use and uses that LEAF_PRIVATE_KEY to generate a “Certificate Signing Request”, CSR for short, which they will send to a CA Authority to get a signed and trusted LEAF_CERTIFICATE.
- Employees of the CA organization receive a Certificate Signing Request (CSR) from a company like Google that wants to have a website google.com be trusted. The certificate signing request tells the CA organization all the specifics of what the LEAF_CERTIFICATE should have in it and what its’ use will be.
- CA organization employees use the information in the CSR to generate a brand new LEAF_CERTIFICATE and sign that certificate with the INTERMEDIATE_CA_PRIVATE_KEY they have access to.
- CA organization sends a copy of the INTERMEDIATE_CA_CERTIFICATE and the newly generated LEAF_CERTIFICATE to the requesting organization (in this case Google).
Notice the private keys in this process were never sent over the Internet in any way. Google generated its own LEAF_PRIVATE_KEY but only sent the CSR to the CA. The CA generated all their own private keys and only used them to sign other things but the private keys never left the CA organization. So far so good, none of the private keys have been sent over the Internet (no possibility of being intercepted) and now all the certificates are signed and ready for use. The browsers have received copies of the CA_ROOT_CERTIFICATE that is self signed by a theoretically un-stealable private key. We have a copy of the INTERMEDIATE_CA_CERTIFICATE that is signed by the CA_ROOT_PRIVATE_KEY and we have the newly generated google.com LEAF_CERTIFICATE that is signed by the INTERMEDIATE_CA_PRIVATE_KEY.
Now when we connect to google.com and it signs something with it’s private key we can decide if we trust that signature by testing:
Do we trust this signature from google.com? Don’t know,
Do we trust the google.com LEAF_CERTIFICATE? Don’t know,
Do we trust the INTERMEDIATE_CA_CERTIFICATE? Don’t know,
Do we trust the CA_ROOT_CERTIFICATE? YES!
Since we trust the CA_ROOT_CERTIFICATE and the CA_ROOT_PRIVATE_KEY signed the intermediate CA.. Now can we trust the INTERMEDIATE_CA_CERTIFICATE? YES!
OK and if we trust the INTERMEDIATE_CA_CERTIFICATE and its INTERMEDIATE_CA_PRIVATE_KEY signed the google.com LEAF_CERTIFICATE… Now can we trust google.com LEAF_CERTIFICATE? YES!
Finally since we trust the google.com LEAF_CERTIFICATE now we know we can trust things signed by the LEAF_PRIVATE_KEY associated with that LEAF_CERTIFICATE!
That is the chain of trust.
How does one know which certs to load into their application?
In most cases all that needs to be loaded in your client applications is the CA_ROOT_CERTIFICATE. The RFC for certificate distribution by servers says “Servers MUST send their entire cert chain with the only optional cert being the ROOT CA”. Browsers and clients are already expected to have a copy of the root CA available so the servers do not have to send that during a TLS connection. HOWEVER… and here’s the catch, not all servers follow the spec. When this happens then it falls to the client to track down the cert that signed the last cert in the chain that the server did send and load that cert, and any other certs in the chain of trust up to and including the Root CA.
If you have any questions or run into any issues, contact us at facts@wolfssl.com, or call us at +1 425 245 8247.


 Is your team looking for a 32-bit MCU that boasts advanced security, performance, and connectivity for your next project in industrial / building automation, automotive or IoT?
Is your team looking for a 32-bit MCU that boasts advanced security, performance, and connectivity for your next project in industrial / building automation, automotive or IoT?
