
Recently we announced that wolfSSL’s Kyber ML-KEM Implementation now Included free of charge for commercial customers. Our PQ Kyber implementation works on nearly any size of device, including the Espressif ESP32. Here are the instructions on configuring the test server and client:
ESP32 Server Application Settings
To enable Kyber, just add these lines to the user_settings.h file:
#define WOLFSSL_EXPERIMENTAL_SETTINGS #define WOLFSSL_HAVE_KYBER #define WOLFSSL_WC_KYBER #define WOLFSSL_SHA3
Next, in the code after the creation of an ssl object:
ssl = wolfSSL_new(ctx));
Simply add this line:
wolfSSL_UseKeyShare(ssl, WOLFSSL_P521_KYBER_LEVEL5);
If successful, the function will return a code of SSL_SUCCESS.
The listening server needs a minimum stack size of approximately 10K bytes.
Linux Client Application Settings
To test with the wolfSSL client, configure wolfSSL to enable the experimental Kyber features:
./configure --enable-kyber=all --enable-experimental
Connect to the listening ESP32 server like this:
./examples/client/client -h 192.168.1.38 -v 4 \
-l TLS_AES_128_GCM_SHA256 \
--pqc KYBER_LEVEL5
The resulting output should look like this:
Using Post-Quantum KEM: KYBER_LEVEL5 SSL version is TLSv1.3 SSL cipher suite is TLS_AES_128_GCM_SHA256 I hear you fa shizzle!
Linux Server Application Settings
To test with the wolfSSL client, configure wolfSSL as shown above for the client, and use this example:
./examples/server/server -v 4 \
-l TLS_AES_128_GCM_SHA256
--pqc KYBER_LEVEL5
The TLS 1.3 server will quietly listen on port 11111. Upon a successful connection from a client, the resulting output should look something like this:
Using Post-Quantum KEM: KYBER_LEVEL5 SSL version is TLSv1.3 SSL cipher suite is TLS_AES_128_GCM_SHA256 Client message: hello wolfssl!
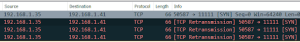
Keep in mind various local firewall rules may need to be adjusted to allow a port 11111 connection. How to determine if there’s a firewall issue? Check WireShark for TCP Retransmission packets that might look something like this:
Are you interested in trying our Post Quantum in your project? Let us know!
Find out more
If you have any feedback, questions, or require support, please don’t hesitate to reach out to us via facts@wolfSSL.com, call us at +1 425 245 8247, or open an issue on GitHub.
Download wolfSSL Now

