You may be aware that wolfSSL has our own implementation of NIST’s ML-KEM, also known as Kyber. ML-KEM is the post-quantum KEM that is slated for standardization by NIST. While the standard is not complete yet, and we have not yet released our implementation into open source, we do have some benchmarking results to share.
Additionally, we should note some things about our implementation that make it unique and useful:
- It will be fully integrated with our other products, including wolfSSL, wolfBoot, curl, etc.
- It is a consumer of our highly optimized SP Math library, with more ML-KEM optimizations to come!
- Because our products are well integrated with many other open source packages, those packages can inherit Kyber/ML-KEM support.
- It supports bare metal, as well as all of the other operating systems we support, including FreeRTOS, VxWorks, Integrity, Zephyr, Itron, LynxOS, etc.
- It also supports all of the silicon targets we support, including ARM, RISCV, DSPs, FPGAs, intel, etc.
The benchmarks results follow:
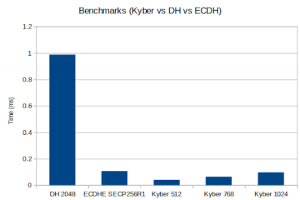
Math: Multi-Precision: Wolf(SP) no-dyn-stack word-size=64 bits=4096 sp_int.c Single Precision: ecc 256 384 521 rsa/dh 2048 3072 4096 asm sp_arm64.c wolfCrypt Benchmark (block bytes 1048576, min 1.0 sec each) DH 2048 key gen 3997 ops took 1.000 sec, avg 0.250 ms, 3996.812 ops/sec DH 2048 agree 4100 ops took 1.001 sec, avg 0.244 ms, 4097.522 ops/sec KYBER512 128 key gen 96100 ops took 1.001 sec, avg 0.010 ms, 96037.765 ops/sec KYBER512 128 encap 78000 ops took 1.000 sec, avg 0.013 ms, 77970.220 ops/sec KYBER512 128 decap 58900 ops took 1.001 sec, avg 0.017 ms, 58867.158 ops/sec KYBER768 192 key gen 58200 ops took 1.000 sec, avg 0.017 ms, 58192.314 ops/sec KYBER768 192 encap 48700 ops took 1.001 sec, avg 0.021 ms, 48664.334 ops/sec KYBER768 192 decap 38100 ops took 1.001 sec, avg 0.026 ms, 38059.656 ops/sec KYBER1024 256 key gen 37800 ops took 1.003 sec, avg 0.027 ms, 37704.299 ops/sec KYBER1024 256 encap 32600 ops took 1.001 sec, avg 0.031 ms, 32566.427 ops/sec KYBER1024 256 decap 26000 ops took 1.001 sec, avg 0.039 ms, 25967.020 ops/sec ECC [ SECP256R1] 256 key gen 84100 ops took 1.001 sec, avg 0.012 ms, 84013.469 ops/sec ECDHE [ SECP256R1] 256 agree 24400 ops took 1.004 sec, avg 0.041 ms, 24300.995 ops/sec
The benchmarks were run on an Apple MacBook Pro 18,3 with an Apple M1 Pro, 3.09 GHz processor. Only 1 core was used. If you want to get the benchmark harness code, then ping us at facts@wolfSSL.com.
This data shows that for Kyber/ML-KEM, algorithm execution performance is rock solid. If you compare Kyber/ML-KEM’s numbers against DH and ECDHE, Kyber holds its own. To understand how to analyze and compare these number, see https://www.wolfssl.com/benchmarks-kyber-level-1-pqm4-integration-stm32-arm-cortex-m4/.
Interested in learning more about our post-quantum efforts? Want to understand how Kyber fits into different protocols and how it might affect your use case? Contact us at wolfSSL by emailing facts@wolfSSL.com or calling us at +1 425 245 8247 to reach out to your regional wolfSSL business director
Download wolfSSL Now

