RECENT BLOG NEWS
strongSwan + wolfSSL + FIPS!
As some may be aware, wolfSSL added support for strongSwan in April of 2019. The upstream commit can be reviewed here: https://github.com/strongswan/strongswan/pull/133
Users can test the latest development master of wolfSSL with the latest version of strongSwan using the following setup:
wolfSSL Build and Installation Steps
$ git clone https://github.com/wolfSSL/wolfssl.git $ cd wolfssl $ ./autogen.sh $ ./configure --enable-opensslall --enable-keygen --enable-rsapss --enable-des3 --enable-dtls --enable-certgen --enable-certreq --enable-certext --enable-sessioncerts --enable-crl --enable-ocsp CFLAGS="-DWOLFSSL_DES_ECB -DWOLFSSL_LOG_PRINTF -DWOLFSSL_PUBLIC_MP -DHAVE_EX_DATA" $ make $ make check $ sudo make install
strongSwan Build and Installation Steps
# if the following packages are not already installed: $ sudo apt-get install flex bison byacc libsoup2.4-dev gperf $ git clone https://github.com/strongswan/strongswan.git $ cd strongswan $ ./autogen.sh # if packages are missing autogen.sh must be re-run $ ./configure --disable-defaults --enable-pki --enable-wolfssl --enable-pem $ make $ make check $ sudo make install
wolfSSL has had interest in enabling FIPS 140-2/140-3 support with strongSwan so our engineers verified everything is working with the wolfCrypt FIPS 140-2 validated Module!
The steps wolfSSL used for testing are as follows:
Testing was done using the wolfSSL commercial FIPS release v4.7.0 which internally uses the wolfCrypt v4.0.0 FIPS 140-2 validated Crypto Module. It was located in the /home/user-name/Downloads directory on the target test system, Linux 4.15 Ubuntu 18.04 LTS running on Intel(R) Xeon(R) CPU E3-1270 v6 @ 3.80GHz.
- wolfSSL was configured and installed with these settings:
./configure --enable-opensslall --enable-keygen --enable-rsapss --enable-des3 --enable-dtls --enable-certgen --enable-certreq --enable-certext --enable-sessioncerts --enable-crl --enable-ocsp CFLAGS="-DWOLFSSL_DES_ECB -DWOLFSSL_LOG_PRINTF -DWOLFSSL_PUBLIC_MP -DHAVE_EX_DATA -DFP_MAX_BITS=8192" --enable-ed25519 --enable-curve25519 --enable-fips=v2 --enable-intelasm --prefix=$(pwd)/../fips-install-dir make make install
- A custom install location was used which equated to
/home/user-name/Downloads/fips-install-dirand the configuration for strongSwan accounted for this. - strongSwan was cloned to
/home/user-name/Downloadswith “git clone https://github.com/strongswan/strongswan.git” - StongSwan was configured and installed with these settings:
./configure --disable-defaults --enable-pki --enable-wolfssl --enable-pem --prefix=$(pwd)/../strongswan-install-dir wolfssl_CFLAGS="-I$(pwd)/../fips-install-dir/include" wolfssl_LIBS="-L$(pwd)/../fips-install-dir/lib -lwolfssl" make make install make check
- In the make check stage of the test, it was observed that 1 test was failing.
Passed 34 of 35 'libstrongswan' suites FAIL: libstrongswan_tests ================== 1 of 1 test failed ==================
- Reviewing the logs it was apparent one of the RSA tests was failing.
- Upon further debugging it turned out the failure was a test in strongSwan that was attempting to create an RSA key size of 1536-bits.
Running case 'generate': DEBUG: key_sizes[_i] set to 1024 + PASS DEBUG: key_sizes[_i] set to 1536 - FAIL DEBUG: key_sizes[_i] set to 2048 + PASS DEBUG: key_sizes[_i] set to 3072 + PASS DEBUG: key_sizes[_i] set to 4096 + PASS
wolfSSL has a function RsaSizeCheck() which in FIPS mode will specifically reject any non FIPS RSA key sizes so this failure was not only expected, but it is a good thing for those wanting to use strongSwan in FIPS mode and ensure only FIPS-validated RSA key sizes will be supported!
wolfSSL is pleased that with the latest release of wolfSSL v4.7.0 and the wolfCrypt FIPS 140-2 module validated on FIPS certificate 3389, strongSwan support is working splendidly and wolfSSL engineers will be making efforts to ensure continued support into the future!
If you have any questions or run into any issues, contact us at facts@wolfssl.com, or call us at +1 425 245 8247.
Who’s testing that cryptography on your platform? With your hardware encryption? With your secure element?
Three of our biggest engineering investments at wolfSSL are testing, testing, and testing. We invest heavily in testing, so that you don’t have to. We develop and test with 30+ operating systems, 10+ compilers, 50+ chipsets, 20+ hardware encryption IP schemes, and 15+ secure enclaves. We add more of the above to our Jenkins based CI/CD package every day. We do unit tests on everything, we run 5 static analyzers, and we run 7 internal fuzz testers. We employ sophisticated outside consultants to run additional fuzz testing.
Oh, yeah, we’ve had our code audited by every major vendor in computing, because they are all our customers, and need to review our code to ensure their own security and branding.
We’ve also been audited by over 20 security research teams in academia.
Finally, we’ve been through industry specific testing like DO-178 in aviation, MISRA and ASPICE in automotive, and FIPS 140 in government.
Contrast all of that with the testing and assurance you get from our competitors on your particular platform. It won’t compare.
Want to hear more about why we have the best tested cryptography and TLS 1.3? Email us at facts at wolfSSL dot com!
If you have any questions or run into any issues, contact us at facts@wolfssl.com, or call us at +1 425 245 8247.
wolfSSL Supports Stunnel 5.57
wolfSSL is happy to announce support for the latest stable version of stunnel, version 5.57. Per the stunnel website, “Stunnel is a proxy designed to add TLS encryption functionality to existing clients and servers without any changes in the programs’ code.” wolfSSL also supports version 5.40 of stunnel. If you’re in need of a fast, low memory, and FIPS-validated TLS 1.3 implementation for stunnel.
If you have any questions or run into any issues, contact us at facts@wolfssl.com, or call us at +1 425 245 8247.
wolfMQTT Release v1.8.0
The winter release of wolfMQTT, v1.8.0, is now available! This release has several bug fixes and optimizations including:
- Fixes for non-blocking in WIN32 and large payload (PR #202)
- Make TLS IO callback functions public (PR #201)
- Bug fixes (PR #186, 188, 189, 193, 196, 199, 200)
- Update default test broker (PR #194)
- MQTT-SN fixes for multithread and register topic name (PR #185, 190)
- Fix multi-thread to use pthread mutex with condition (PR #183)
- Fix for WIN thread create macro (PR #182)
- Use options.h with Arduino build (PR #181)
- Use MqttClient_Ping_ex instead of MqttClient_Ping in examples (PR #179)
- Fixes for building with MinGW (PR #178)
- MQTT-SN support for multithread (PR #176)
- TLS mutual auth in client examples (PR #175)
- MQTT-SN feature enhancements (PR #173)
- Add runtime message option to client (PR #171)
If you have any questions or run into any issues, contact us at facts@wolfssl.com, or call us at +1 425 245 8247.
https://github.com/wolfSSL/wolfMQTT/blob/master/ChangeLog.md
While you’re there, show us some love and give the wolfMQTT project a Star!
You can download the latest release here: https://www.wolfssl.com/download/
Or clone directly from our GitHub repository: https://github.com/wolfSSL/wolfMQTT
Wondering how well the Apple M1 will run cryptography? Us too!
Hi! We’ve been wondering how well the M1 will perform in our standard cryptographic benchmarks, just like you! We’ll also be bring FIPS 140-2 to the M1.
Watch this space, as we’ll be releasing them in the next few weeks.
If you have any questions or run into any issues, contact us at facts@wolfssl.com, or call us at +1 425 245 8247.
wolfSSL ARMv8 Support
Did you know that the wolfSSL embedded SSL/TLS library supports ARMv8 as well as the Cryptography Extensions that it provides? wolfSSL is more than 10 times faster with AES and SHA256 operations the ARMv8 board we have been testing on (HiKey LeMaker) when using hardware acceleration versus software crypto!
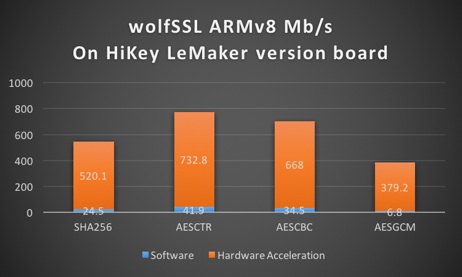
ARMv8 Benchmark Data comparing Software and Hardware Cryptography
| Algorithm | Software Cryptography | Hardware Cryptography |
|---|---|---|
| RNG | 16.761 MB/s | 82.599 MB/s |
| AES-128-CBC-enc | 26.491 MB/s | 649.179 MB/s |
| AES-128-CBC-dec | 26.915 MB/s | 607.407 MB/s |
| AES-192-CBC-enc | 22.796 MB/s | 566.717 MB/s |
| AES-192-CBC-dec | 23.130 MB/s | 553.092 MB/s |
| AES-256-CBC-enc | 20.004 MB/s | 504.143 MB/s |
| AES-256-CBC-dec | 20.207 MB/s | 491.374 MB/s |
| AES-128-GCM-enc | 6.224 MB/s | 393.407 MB/s |
| AES-128-GCM-dec | 6.226 MB/s | 182.279 MB/s |
| AES-192-GCM-enc | 5.895 MB/s | 361.801 MB/s |
| AES-192-GCM-dec | 5.895 MB/s | 175.676 MB/s |
| AES-256-GCM-enc | 5.609 MB/s | 333.911 MB/s |
| AES-256-GCM-dec | 5.610 MB/s | 169.085 MB/s |
| CHACHA | 60.510 MB/s | 60.017 MB/s |
| CHA-POLY | 41.805 MB/s | 41.410 MB/s |
| MD5 | 156.310 MB/s | 154.421 MB/s |
| POLY1305 | 144.464 MB/s | 143.058 MB/s |
| SHA | 89.874 MB/s | 89.154 MB/s |
| SHA-256 | 38.805 MB/s | 533.139 MB/s |
| HMAC-MD5 | 156.301 MB/s | 154.083 MB/s |
| HMAC-SHA | 89.859 MB/s | 89.045 MB/s |
| HMAC-SHA256 | 38.814 MB/s | 532.316 MB/s |
| RSA, 2048, public | 171.995 Ops/s | 171.355 Ops/s |
| RSA, 2048, private | 13.716 Ops/s | 13.686 Ops/s |
| DH, 2048, key generation | 50.831 Ops/s | 50.575 Ops/s |
| DH, 2048, agree | 41.826 Ops/s | 41.596 Ops/s |
If you have any questions or run into any issues, contact us at facts@wolfssl.com, or call us at +1 425 245 8247.
wolfSSL Version 4.7.0 Is Available!
Version 4.7.0 of wolfSSL has general fixes and optimizations, a few excellent feature additions, and some vulnerability fixes. Some of the new features added are support for S/MIME bundles which are commonly used with email traffic, an --enable-reproducable-build flag to help out with inspecting the wolfSSL library created, expansion to the OpenSSL compatibility layer, and additional session ticket API’s that help modularly control which TLS protocol version can use session tickets.
A few of the improvements and optimizations in the release are to linux kernel module support, DTLS resending of a flight after timeouts, the CMake build with a user settings file and out of directory builds of wolfSSL.
This release fixes 3 vulnerabilities, one of them being a TLS 1.3 client side issue that is rated as high. Thanks to Aina Toky Rasoamanana and Olivier Levillain from Télécom SudParis for the report on this TLS 1.3 issue.
A full list of items in the release can be seen in the ChangeLog.md bundled with wolfSSL or on our main webpage.
If you have any questions or run into any issues, contact us at facts@wolfssl.com, or call us at +1 425 245 8247.
FIPS certificate #2425 is being added to NIST sunset list: wolfSSL customers can achieve effortless transition to FIPS cert #3389
FIPS 140-2 requires the use of validated cryptography in the security systems implemented by federal agencies to protect sensitive information. The wolfCrypt Module is a comprehensive suite of FIPS Approved algorithms. All key sizes and modes have been implemented to allow flexibility and efficiency.
The National Institute of Standards and Technology (NIST) is sending FIPS cert #2425 into sunset June 2021. For customers who will be impacted, the wolfCrypt Cryptographic Module maintains its #3389 certificate and can be used in conjunction with the wolfSSL embedded SSL/TLS library for full TLS 1.3 client and server support. Upgrade your FIPS cert with wolfSSL to stay afloat and benefit from:
- Algorithm support for TLS 1.3!
- New algorithms such as AES (CBC, GCM, CTR, ECB), CVL, Hash DRBG, DSA, DHE, ECDSA (key generation, sign, verify), HMAC, RSA (key generation, sign, verify), SHA-3, SHA-2, SHA-1, and Triple-DES
- Hardware encryption support for NXP’s Cryptographic Assistance and Assurance Module (CAAM), NXP Memory-Mapped Cryptographic Acceleration Unit (mmCAU), Intel’s AES-NI, and more
- Support for secure elements and TPM’s
- Interoperability with wolfBoot, wolfSSH, and wolfTPM
- Integration support for third party libraries such as strongswan, nginx, python and more
Contact us to upgrade to FIPS cert #3389 at fips@wolfssl.com.
Additional Resources
Learn more about wolfSSL support for FIPS cert #3389: https://www.wolfssl.com/wolfcrypt-fips-certificate-3389-3/
For a list of supported Operating Environments for wolfCrypt FIPS, check our FIPS page: https://www.wolfssl.com/license/fips/
Our FIPS Story
wolfSSL is currently the leader in embedded FIPS certificates. We have a long history in FIPS starting with wolfCrypt FIPS 140-2 Level 1 Certificate #2425 as well as wolfCrypt v4 FIPS 140-2 Level 1 Certificate #3389. wolfSSL partners with FIPS experts KeyPair to bring you FIPS consulting services, and high assurance along each step of your FIPS certification process. Additionally, wolfSSL will be the first implementation of FIPS 140-3.
wolfSSL also provides support for a wolfCrypt FIPS Ready version of the library! wolfCrypt FIPS Ready is our FIPS enabled cryptography layer code included in the wolfSSL source tree that you can enable and build. You do not get a FIPS certificate, you are not FIPS approved, but you will be FIPS Ready. FIPS Ready means that you have included the FIPS code into your build and that you are operating according to the FIPS enforced best practices of default entry point, and power on self test.
wolfCrypt FIPS Ready can be downloaded from the wolfSSL download page located here: https://www.wolfssl.com/download/. More information on getting set up with wolfCrypt FIPS Ready can be found in our FIPS Ready User guide here: https://www.wolfssl.com/docs/fips-ready-user-guide/
If you have any questions or run into any issues, contact us at facts@wolfssl.com, or call us at +1 425 245 8247.
wolfSSL CMSIS Pack
As a proud partner with ARM, wolfSSL is available as a CMSIS pack! wolfSSL was one of the first libraries available as a MDK5 software pack, which has evolved into CMSIS.
The wolfSSL ARM MDK5 pack supports CMSIS-RTOS by default, providing both the library and example applications. The user can choose to use a different OS as well.
If you have any questions or run into any issues, contact us at facts@wolfssl.com, or call us at +1 425 245 8247.
TPM 2.0 Library comparison, build size and memory usage
A question we get asked frequently is what are the build size and memory usage of the wolfTPM portable library. Here we will compare wolfTPM with the other popular TPM2.0 stacks, “ibmtss2” created at IBM and “tpm2-tss” originally created by Intel.
This comparison is interesting, because wolfTPM was built from scratch to be optimized for embedded devices and resource-constrained environments. This gives our TPM2.0 library a small footprint while still providing the features our users want and need.
At the time of writing, the current versions of TPM2.0 libraries is as follows:
wolfTPM is at major version 2.0.0
ibmtss2 is at version 1.5.0
tss2-tpm is at version 3.0.3
The test environment is x86_64 machine, running Ubuntu 20.04.1 LTS, with gcc compiler at version 9.3.0 (from the official Ubuntu 9.3.0-17ubuntu1~20.04 package).
Here are the memory footprint results reported by the GNU Size tool:
| Code (text) | Memory (data) | bss | Total (Dec) | filename |
|---|---|---|---|---|
| 2658649 | 186120 | 186120 | 2879905 | ibmtss keygen |
| 2730620 | 176736 | 33888 | 2941244 | Tpm2-tss keygen |
| 119980 | 1040 | 24 | 121044 | wolfTPM keygen |
Observations
- wolfTPM needs the least amount of RAM, in orders of magnitude.
- wolfTPM also has the smallest build size
- wolfTPM does not use heap
- wolfTPM has no external dependencies
For completeness, below are the configurations used for each TPM2.0 stack:
– tpm2-tss stack (originally created by Intel) was built using
./configure –enable-shared=no –enable-nodl –disable-fapi -disable-tcti-mssim -disable-tcti-swtpm
In details:
- Disable shared library build (enables static library build)
- Disable dynamic library loading
- Disable support of feature api
- Disable support for Microsoft TPM Simulator
- Disable support for IBM TPM Simulator
tpm2-tss test application: https://github.com/tomoveu/tpm2-tss/tree/size-9
– Ibmtss stack was built using
./configure –disable-tpm-1.2 –disable-rmtpm –disable-shared
In details:
- Disable support for obsolete TPM 1.2
- Disable support for resource manager
- Disable shared libraries (enables static library build)
ibmtss test application: https://github.com/tomoveu/ibmtss/tree/ibm-size-3
– wolfTPM was built using
./configure –enable-devtpm –enable-wolfcrypt –disable-shared
In details:
- Enable /dev/tpmX interface for Linux
- Enable wolfCrypt support for parameter encryption
- Disable shared libraries (enables static library build)
wolfTPM test application: https://github.com/tomoveu/wolfTPM/tree/size-6
If you have any questions or run into any issues, contact us at facts@wolfssl.com, or call us at +1 425 245 8247.
For a full list of wolfTPM features, please visit the wolfTPM Product Page.
Weekly updates
Archives
- June 2025 (21)
- May 2025 (25)
- April 2025 (24)
- March 2025 (22)
- February 2025 (21)
- January 2025 (23)
- December 2024 (22)
- November 2024 (29)
- October 2024 (18)
- September 2024 (21)
- August 2024 (24)
- July 2024 (27)
- June 2024 (22)
- May 2024 (28)
- April 2024 (29)
- March 2024 (21)
- February 2024 (18)
- January 2024 (21)
- December 2023 (20)
- November 2023 (20)
- October 2023 (23)
- September 2023 (17)
- August 2023 (25)
- July 2023 (39)
- June 2023 (13)
- May 2023 (11)
- April 2023 (6)
- March 2023 (23)
- February 2023 (7)
- January 2023 (7)
- December 2022 (15)
- November 2022 (11)
- October 2022 (8)
- September 2022 (7)
- August 2022 (12)
- July 2022 (7)
- June 2022 (14)
- May 2022 (10)
- April 2022 (11)
- March 2022 (12)
- February 2022 (22)
- January 2022 (12)
- December 2021 (13)
- November 2021 (27)
- October 2021 (11)
- September 2021 (14)
- August 2021 (10)
- July 2021 (16)
- June 2021 (13)
- May 2021 (9)
- April 2021 (13)
- March 2021 (24)
- February 2021 (22)
- January 2021 (18)
- December 2020 (19)
- November 2020 (11)
- October 2020 (3)
- September 2020 (20)
- August 2020 (11)
- July 2020 (7)
- June 2020 (14)
- May 2020 (13)
- April 2020 (14)
- March 2020 (4)
- February 2020 (21)
- January 2020 (18)
- December 2019 (7)
- November 2019 (16)
- October 2019 (14)
- September 2019 (18)
- August 2019 (16)
- July 2019 (8)
- June 2019 (9)
- May 2019 (28)
- April 2019 (27)
- March 2019 (15)
- February 2019 (10)
- January 2019 (16)
- December 2018 (24)
- November 2018 (9)
- October 2018 (15)
- September 2018 (15)
- August 2018 (5)
- July 2018 (15)
- June 2018 (29)
- May 2018 (12)
- April 2018 (6)
- March 2018 (18)
- February 2018 (6)
- January 2018 (11)
- December 2017 (5)
- November 2017 (12)
- October 2017 (5)
- September 2017 (7)
- August 2017 (6)
- July 2017 (11)
- June 2017 (7)
- May 2017 (9)
- April 2017 (5)
- March 2017 (6)
- January 2017 (8)
- December 2016 (2)
- November 2016 (1)
- October 2016 (15)
- September 2016 (6)
- August 2016 (5)
- July 2016 (4)
- June 2016 (9)
- May 2016 (4)
- April 2016 (4)
- March 2016 (4)
- February 2016 (9)
- January 2016 (6)
- December 2015 (4)
- November 2015 (6)
- October 2015 (5)
- September 2015 (5)
- August 2015 (8)
- July 2015 (7)
- June 2015 (9)
- May 2015 (1)
- April 2015 (4)
- March 2015 (12)
- January 2015 (4)
- December 2014 (6)
- November 2014 (3)
- October 2014 (1)
- September 2014 (11)
- August 2014 (5)
- July 2014 (9)
- June 2014 (10)
- May 2014 (5)
- April 2014 (9)
- February 2014 (3)
- January 2014 (5)
- December 2013 (7)
- November 2013 (4)
- October 2013 (7)
- September 2013 (3)
- August 2013 (9)
- July 2013 (7)
- June 2013 (4)
- May 2013 (7)
- April 2013 (4)
- March 2013 (2)
- February 2013 (3)
- January 2013 (8)
- December 2012 (12)
- November 2012 (5)
- October 2012 (7)
- September 2012 (3)
- August 2012 (6)
- July 2012 (4)
- June 2012 (3)
- May 2012 (4)
- April 2012 (6)
- March 2012 (2)
- February 2012 (5)
- January 2012 (7)
- December 2011 (5)
- November 2011 (7)
- October 2011 (5)
- September 2011 (6)
- August 2011 (5)
- July 2011 (2)
- June 2011 (7)
- May 2011 (11)
- April 2011 (4)
- March 2011 (12)
- February 2011 (7)
- January 2011 (11)
- December 2010 (17)
- November 2010 (12)
- October 2010 (11)
- September 2010 (9)
- August 2010 (20)
- July 2010 (12)
- June 2010 (7)
- May 2010 (1)
- January 2010 (2)
- November 2009 (2)
- October 2009 (1)
- September 2009 (1)
- May 2009 (1)
- February 2009 (1)
- January 2009 (1)
- December 2008 (1)

