RECENT BLOG NEWS
wolfSSL Use With Hexagon Toolchain
The Qualcomm Hexagon SDK is used for building code to run on DSP processors. Use of the Hexagon toolchain to offload ECC verify operations has been added to wolfSSL. This can free up the main CPU for other operations or lead to future optimizations with HVX on some algorithms that use vector operations. The Makefile for building with the Hexagon toolchain and a README with more information can be found in the directory wolfssl-4.6.0/IDE/HEXAGON.
If you have any questions or run into any issues, contact us at facts@wolfssl.com, or call us at +1 425 245 8247.
What is TPM parameter encryption?
Trusted Platform Modules (TPM) give us a secure vault for storing keys and secrets. We could also use a TPM as root-of-trust for reporting the health and integrity of our servers or bare metal systems (e.g. IoT). However, TPMs are physical devices. The communication between our software and the TPM happens over a physical interface, typically a SPI bus. This physical interface could be attacked maliciously. For example, IoT and Edge devices are exposed at this risk, because they are deployed in the field. An attacker might physically open the device and try to interfere with the communication between our software and the TPM. To protect from this risk, a TPM offers the capability of parameter encryption.
TPM has the ability to receive commands with their first parameter encrypted. If requested, the TPM could also respond with an encrypted first parameter. Usually, the first parameter is where the most sensitive data of a TPM command is stored. For example, during a TPM2_Create for generating a new key pair, the authValue used as password for the new key is stored in a structure called inSensitive that is the very first parameter of a TPM2_Create command request. All of this should be handled by the TPM stack. Because in order to use parameter encryption a TPM session must be set.
wolfTPM recently added parameter encryption support for protection of man-in-the-middle (MITM) attacks and offers new API wrappers to simplify its use. There is now the wolfTPM2_StartSesssion wrapper to start TPM sessions for parameter encryption and wolfTPM2_SetAuth to make use of this session. Regardless, if you want to use this extra layer of protection or not, the wolfTPM2_CreateKey wrapper accepts the same number of parameters. This way the development cycle is not affected, if you want to add MITM protection to your secure application by using wolfTPM.
TPM supports AES CFB and XOR method for parameter encryption, and wolfTPM supports both. All the encryption and decryption of command parameters is handled by the stack. The secure exchange of secrets for setting up the TPM session for parameter encryption also happens seamlessly from the developer’s perspective.
If you have any questions or run into any issues, contact us at facts@wolfssl.com, or call us at +1 425 245 8247.
wolfSSL adds Silicon Labs Hardware acceleration support
wolfSSL is excited to announce support for using Silicon Labs Hardware acceleration. The EFR32 family of devices support multiple wireless interfaces with hardware cryptographic operations. wolfSSL can now offload cryptographic operations for dramatically increased performance on the Silicon Labs EFR32 family!
Our new support includes hardware acceleration of the following algorithms:
- RNG
- AES-CBC
- AES-GCM
- AES-CCM
- SHA-1
- SHA-2
- ECDHE
- ECDSA
The new functionality can be enabled by defining WOLFSSL_SILABS_SE_ACCEL. In user_settings.h More details are available in the README.md in wolfcrypt/src/port/silabs of the wolfSSL tree.
Benchmarks
Benchmark was performed on an EFR32 Gecko 2 (Series 1) using the xGM210P022.
The tests use Simplicity Studio v5 with Gecko SDK 3.0 using Micrium OS 5 and Secure Element Manager.
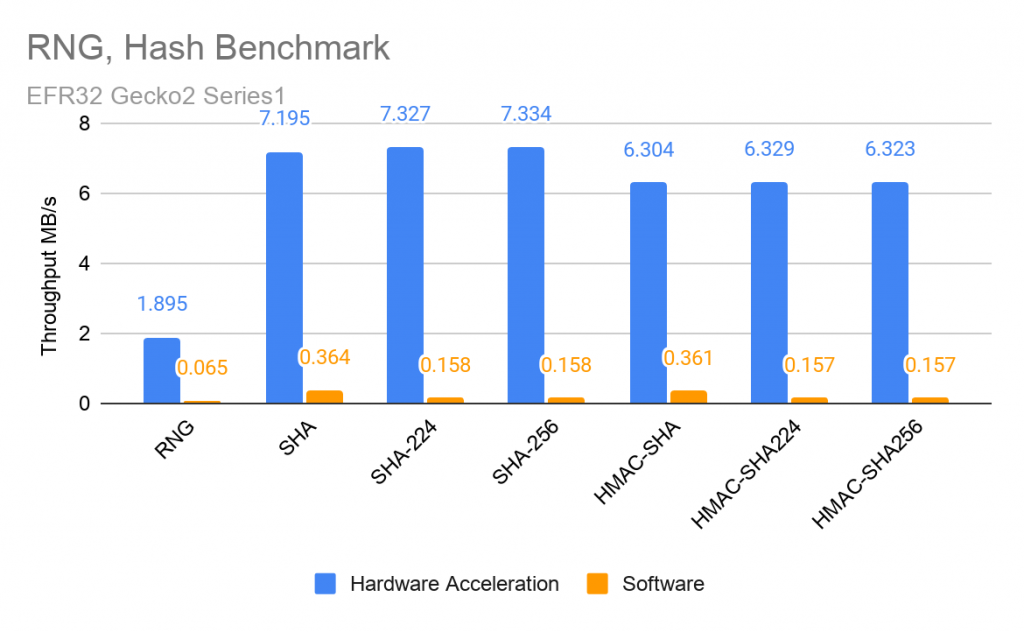
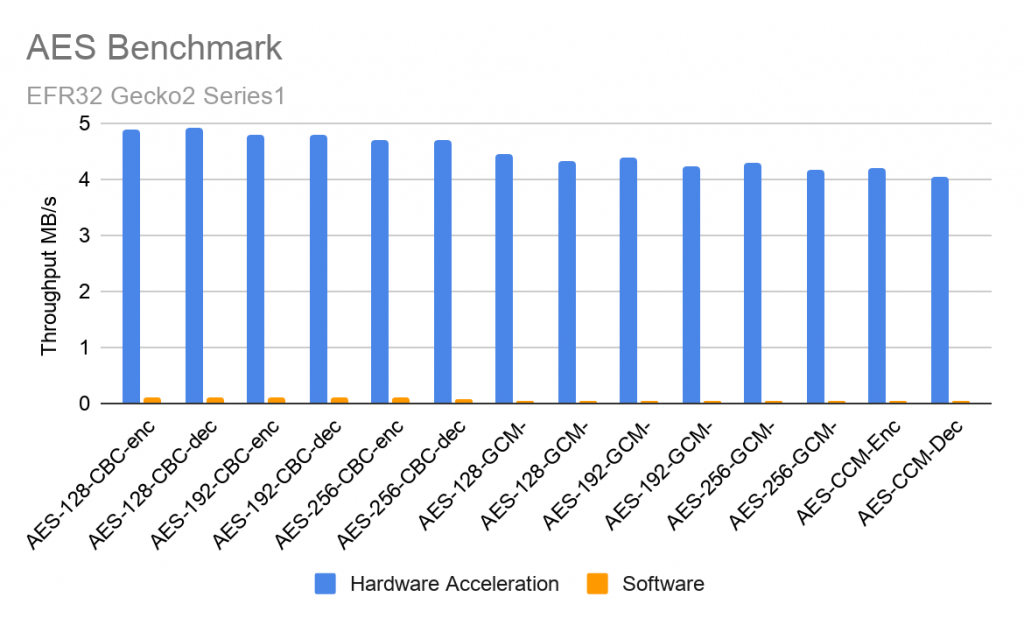
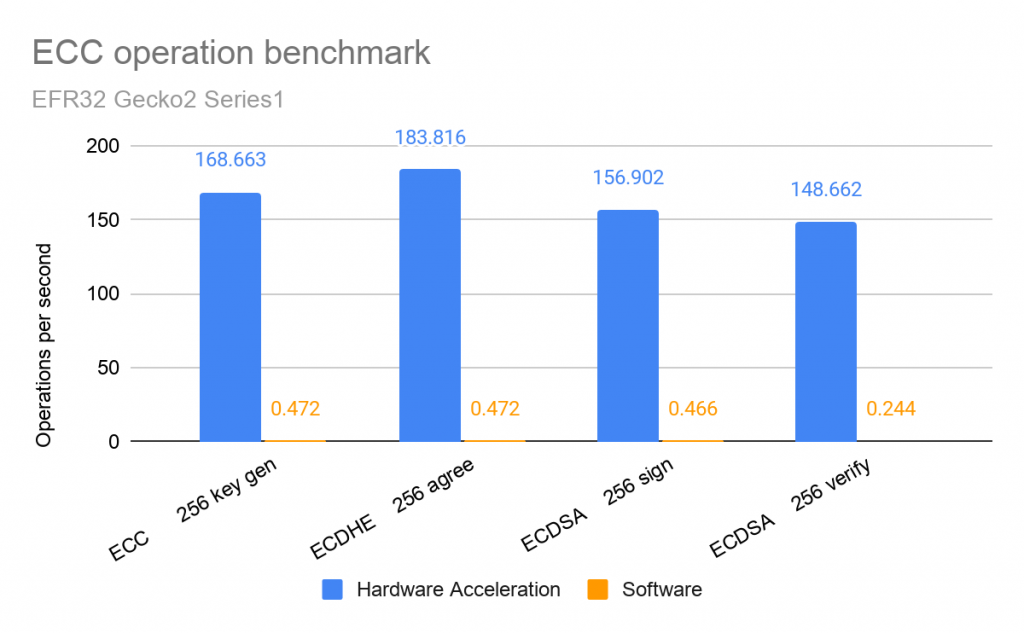
| Algorithm | Data Throughput (MB/s) |
| RNG | 1.895 |
| SHA | 7.195 |
| SHA-224 | 7.327 |
| SHA-256 | 7.334 |
| HMAC-SHA | 6.304 |
| HMAC-SHA224 | 6.329 |
| HMAC-SHA256 | 6.323 |
| AES-128-CBC-enc | 4.897 |
| AES-128-CBC-dec | 4.907 |
| AES-192-CBC-enc | 4.795 |
| AES-192-CBC-dec | 4.805 |
| AES-256-CBC-enc | 4.703 |
| AES-256-CBC-dec | 4.712 |
| AES-128-GCM-enc | 4.463 |
| AES-128-GCM-dec | 4.317 |
| AES-192-GCM-enc | 4.377 |
| AES-192-GCM-dec | 4.235 |
| AES-256-GCM-enc | 4.297 |
| AES-256-GCM-dec | 4.162 |
| AES-CCM-Enc | 4.203 |
| AES-CCM-Dec | 4.045 |
| ECC operation | Average time to complete (ms) | Operations per second |
| ECC 256 key gen | 5.929 | 168.663 |
| ECDHE 256 agree | 5.440 | 183.816 |
| ECDSA 256 sign | 6.373 | 156.902 |
| ECDSA 256 verify | 6.727 | 148.662 |
If you have any questions or run into any issues, contact us at facts@wolfssl.com, or call us at +1 425 245 8247.
wolfSSL Cisco libest Port
With wolfSSL 4.6.0, the cisco/libest EST library has been ported to work with wolfSSL. The Enrollment over Secure Transport (EST) protocol defines “enrollment for clients using Certificate Management over CMS (CMC) [RFC5272] messages over a secure transport.” It uses TLS >1.1 and the Hypertext Transfer Protocol (HTTP) to facilitate secure and authenticated Public Key Infrastructure (PKI) Requests and Responses [RFC5272]. libest is a client and server EST implementation written in C.
To build wolfSSL 4.6.0 for libest:
./configure --enable-libest
make
make install
To obtain a copy of libest that is compatible with wolfSSL, please contact us at support@wolfssl.com.
Once you have a wolfSSL compatible version of libest, to build the library:
./autogen.sh
./configure --enable-wolfssl
make
make install
To run the tests in test/UT configure wolfSSL instead with:
./configure --enable-libest --enable-dsa --enable-oldtls --enable-tlsv10 --enable-sslv3
The porting of libest to wolfSSL has greatly expanded the compatibility layer. Many new API’s were introduced and old ones have been updated. Additionally, Certificate Signing Request (CSR) generation and parsing has been expanded to meet the needs of the libest library. Some of the new changes include:
- Parsing a CSR to be used for certificate generation
- Parsing and generating a limited number of supported CSR attributes
- Parsing configuration files using NCONF APIs
- Retrieving the local and peer finished message contents
- Creating and parsing text databases using TXT_DB API
- New OpenSSL compatibility layer functions implemented
- ASN1_get_object
- d2i_ASN1_OBJECT
- c2i_ASN1_OBJECT
- BIO_new_fd
- BIO_snprintf
- BUF_strdup
- BUF_strlcpy
- BUF_strlcat
- sk_CONF_VALUE_new
- sk_CONF_VALUE_free
- sk_CONF_VALUE_pop_free
- sk_CONF_VALUE_num
- sk_CONF_VALUE_value
- lh_CONF_VALUE_retrieve
- lh_CONF_VALUE_insert
- NCONF_new
- NCONF_free
- NCONF_get_string
- NCONF_get_section
- NCONF_get_number
- NCONF_load
- CONF_modules_load
- _CONF_new_section
- _CONF_get_section
- X509V3_conf_free
- EVP_PKEY_copy_parameters
- EVP_PKEY_get_default_digest_nid
- EVP_PKEY_CTX_ctrl_str
- IMPLEMENT_LHASH_HASH_FN
- IMPLEMENT_LHASH_COMP_FN
- LHASH_HASH_FN
- LHASH_COMP_FN
- lh_strhash
- PKCS12_verify_mac
- i2d_PKCS7_bio
- SSL_get_finished
- SSL_get_peer_finished
- X509_get_ext_by_OBJ
- i2d_X509_REQ_bio
- d2i_X509_REQ_bio
- PEM_read_bio_X509_REQ
- d2i_X509_REQ
- X509_REQ_sign_ctx
- X509_REQ_add1_attr_by_NID
- X509_REQ_add1_attr_by_txt
- X509_REQ_get_attr_by_NID
- X509_REQ_get_attr
- X509_ATTRIBUTE_get0_type
- X509_to_X509_REQ
- X509_get0_extensions
- X509_get_extensions
- X509_REQ_get_extensions
- X509_REQ_get_subject_name
- X509_REQ_get_pubkey
- X509_REQ_set_version
- X509_sign_ctx
- X509_REQ_print
- X509_print_fp
- X509_REQ_print_fp
- X509_signature_print
- X509_get0_signature
- X509_verify
- X509_REQ_verify
- X509_REQ_check_private_key
- X509_delete_ext
- sk_X509_INFO_shift
- X509_NAME_delete_entry
- X509_NAME_print_ex_fp
- X509_STORE_CTX_get0_parent_ctx
- X509_REQ_get_X509_PUBKEY
- BIO_new_connect
- BIO_set_conn_port
- BIO_do_connect
- ASN1_TIME_new
- ASN1_UTCTIME_new
- ASN1_UTCTIME_free
- ASN1_TIME_set
- ASN1_TIME_set_string
- ASN1_TIME_to_string
- a2i_ASN1_INTEGER
- ASN1_STRING_new
- ASN1_STRING_free
- ASN1_STRING_cmp
- ASN1_UNIVERSALSTRING_to_string
- DHparams_dup
- OPENSSL_cleanse
- sk_OPENSSL_STRING_num
- sk_OPENSSL_PSTRING_num
- sk_OPENSSL_PSTRING_value
- sk_OPENSSL_STRING_free
- SSL_CTX_set_srp_strength
- SSL_get_srp_username
- TXT_DB_read
- TXT_DB_write
- TXT_DB_insert
- TXT_DB_free
- TXT_DB_create_index
- TXT_DB_get_by_index
If you have any questions or run into any issues, contact us at facts@wolfssl.com, or call us at +1 425 245 8247.
(D)TLS 1.2 Secure Renegotiation Application Data
One of the new features in wolfSSL 4.6.0 is the ability to process application data during a (D)TLS 1.2 secure renegotiation. The new functionality (added in commit 7c89d10e5362ec281ce61ff12f37a091aa124e98) allows users to send and receive their data during the re-handshake process. Sending data can be accomplished, when using non-blocking sockets, by calling the wolfSSL_write API during a secure renegotiation. To read data during a secure renegotiation, use the wolfSSL_read API.
The wolfSSL examples have been updated to test exchanging application data during a secure renegotiation. To enable and test this new feature, build wolfSSL 4.6.0 with the following commands:
./configure --enable-secure-renegotiation
make
Run the following TLS examples simultaneously in separate windows to demonstrate application data with secure renegotiation:
./examples/server/server -M -m -d -N
./examples/client/client -R -i scr-app-data -N
To run the same tests with DTLS add --enable-dtls to the configure parameters and add -u to both of the example parameters:
./configure --enable-secure-renegotiation --enable-dtls
make
./examples/server/server -M -m -d -N -u
./examples/client/client -R -i scr-app-data -N -u
Users who use secure renegotiation must also expect and handle a new error value. wolfSSL TLS API’s (wolfSSL_connect, wolfSSL_accept, wolfSSL_read, wolfSSL_write) may now return a failure and set the error code to APP_DATA_READY (retrievable by wolfSSL_get_error). This signals to the user that wolfSSL has received application data during a secure renegotiation. The user should immediately call wolfSSL_read to retrieve the received data. If wolfSSL_read is not called immediately after receiving the APP_DATA_READY error code then the data may be dropped if new application data is received. This applies to both TLS and DTLS.
An example connect loop using non-blocking sockets which processes application data during a secure renegotiation:
if ((ret = wolfSSL_Rehandshake(ssl)) != WOLFSSL_SUCCESS) {
err = wolfSSL_get_error(ssl, 0);
if (err == WOLFSSL_ERROR_WANT_READ ||
err == WOLFSSL_ERROR_WANT_WRITE ||
err == APP_DATA_READY) {
do {
if (err == APP_DATA_READY) {
if ((ret = wolfSSL_read(ssl, reply,
sizeof(reply)-1)) < 0) {
/* HANDLE ERROR */
}
printf("Received message during "
"renegotiation: %s\n", reply);
}
err = 0;
if ((ret = wolfSSL_connect(ssl)) != WOLFSSL_SUCCESS) {
err = wolfSSL_get_error(ssl, ret);
}
} while (ret != WOLFSSL_SUCCESS &&
(err == WOLFSSL_ERROR_WANT_READ ||
err == WOLFSSL_ERROR_WANT_WRITE ||
err == APP_DATA_READY));
}
}
Please see the example/client/client.c and example/server/server.c files in the wolfSSL directory as a reference for how the APIs may be used.
If you have any questions or run into any issues, contact us at facts@wolfssl.com, or call us at +1 425 245 8247.
Updated wolfSSL Yocto and OpenEmbedded Recipes
We recently validated the compatibility of our “meta-wolfssl” layer with Yocto 3.0 Zeus, and also updated our wolfSSL recipe to match our newest 4.6.0 release! We offer recipes for wolfSSL, wolfSSH, wolfMQTT, and wolfTPM, all available for Yocto Project or OpenEmbedded based projects.
Adding the wolfSSL products to your project happens in just three steps:
- Clone the git repo from GitHub into your Yocto/OE sources location:
- git clone https://github.com/wolfssl/meta-wolfssl
- Add to your build’s bblayers.conf file the following line, in the BBLAYERS section:
'/path/to/yocto/poky/meta-wolfssl'
- Edit your build’s local.conf and add the following line:
IMAGE_INSTALL_append = "wolfssl wolfssh wolfmqtt wolftpm"
Last, build your preferred target using bitbake and the resulted image will have:
- wolfSSL embedded SSL/TLS library
- wolfSSH lightweight SSH library
- wolfMQTT lightweight MQTT Client Library
- wolfTPM TPM 2.0 Library
If you are interested in trying these recipes out, we have a Getting Started document available here:
wolfSSL Getting Started for Yocto and OpenEmbedded
If you have any questions or run into any issues, contact us at facts@wolfssl.com, or call us at +1 425 245 8247.
wolfSSL RC2-ECB/CBC Support and Integration with PKCS#12
One of the features included in the new wolfSSL 4.6.0 release is support for RC2-ECB/CBC and its integration into wolfSSL’s PKCS#12 functionality.
RC2-ECB/CBC has been added to wolfCrypt for users who have backwards compatibility requirements and may need to interop with older existing applications or devices. This feature is disabled by default and can be enabled with the “--enable-rc2” configure option.
Along with the addition of RC2, wolfSSL now supports parsing and decoding PKCS#12 bundles generated using pbeWithSHA1And40BitRC2-CBC encryption. By default, OpenSSL generates .p12 bundles with pbeWithSHA1And40BitRC2-CBC encryption when using the pkcs12 command. This change now allows wolfSSL to decode those OpenSSL-generated .p12 bundles.
If you have any questions or run into any issues, contact us at facts@wolfssl.com, or call us at +1 425 245 8247.
Modern testing of the wolfSSL TLS library
Guest blog, written by Robert Hörr (e-mail: robert (dot) hoerr (at) t-systems (dot) com)
(Security Evaluator of Deutsche Telekom Security GmbH)
My name is Robert Hörr and I am working as a penetration tester at Deutsche Telekom Security GmbH. Pentesting is mostly done on security software, as for instance the wolfSSL TLS library to discover issues like the Heartbleed bug of OpenSSL. I have discovered some issues in the wolfSSL TLS library (see https://www.wolfssl.com/docs/security-vulnerabilities) using my own developed TLS-FAST (Fast Automated Software Testing) framework. In the future my goal is to provide our customers a FAST service to test their software products.
Why are TLS libraries tested?
It is important to check TLS libraries because TLS is one of the most deployed security protocols in the Internet. Typically, there is no client authentication on a standard Internet server by default configuration, to ensure that every Internet user can use it. Hence, any vulnerability in the TLS protocol implementation can be exploited easily. There are many TLS vulnerability entries in the public CVE list and the number is growing constantly.
Which testing approach is used?
The wolfSSL TLS library is a constantly growing project, with more and more functionalities, extensions and TLS versions added to its scope over time. This offers wolfSSL customers maximal flexibility in the use of the wolfSSL TLS library. Because of this growing process, the source code gets more complex. It is hardly possible to check all code paths by a manual source code review. Hence, dynamic automated machine testing must be performed. An efficient way to perform this kind of testing is the code coverage fuzzing approach. This fuzzing variant allows to discover all code paths. The discovering speed depends on the available computing resources. The code paths are checked systematically for memory leaks, buffer overflows, logical issues and so on.
Which tools are used for TLS testing?
Several open source fuzzing tools, which are based on this fuzzing approach, are public available. Some of the most popular ones are AFL, LibFuzzer and HonggFuzz. The community discovered many issues using any of them. Each of these tools has its strengths in certain fuzzing areas, for example HonggFuzz has a higher number of executions per second than the other tools. To benefit from all fuzzers at the same time, I have developed the FAST (Fast Automated Software Testing) framework for TLS libraries, which combines the strengths of several fuzzing tools. Over the time, the following features and approaches have been added to this framework:
- Deterministic runs:
- The entire testing process is deterministic, so that discovered issues can be reproduced easily.
- Independence:
- The testing process is independent from the environment. So that for example the process can be executed on every operating system.
- Realistic use:
- The TLS libraries are used realistically to discover issues occurring in the field. So for example the original source code and the code paths should not be changed.
- Detection:
- All kinds of implementation issues can be discovered by the testing process. For example buffer overflows or memory leaks are detected by the AddressSanitizer.
- Logical issues or vulnerabilities are discovered by specific TLS tests.
- Scalability:
- The testing process can be scaled linearly by adding more computation and storage resources.
- Coverage:
- Code coverage is used to detect all code paths. If all applicable code paths are identified, the actual testing will start.
- Automation:
- The full testing process runs automatically on a machine. Therefore no manual work is needed anymore.
- Flexibility:
- The framework can be adapted to another tested software. This adaption to a new software takes some hours or days.
How is the wolfSSL TLS library tested?
The wolfSSL TLS library includes several TLS versions, features, extensions and crypto options. The testing focus was mainly defined on the TLS handshake of TLS versions 1.2, 1.3 and their extensions and features, because the TLS handshake implementations include most of the known TLS vulnerabilities (CVEs) and the other TLS versions are not recommended to use anymore.
Currently I am using the TLS-FAST framework for checking the API functions wolfSSL_accept(…) and wolfSSL_connect(…) of the wolfSSL TLS library master branch. This master branch gets the newest updates first. So the master branch must be tested to discover the newly added issues from the updates and to avoid that these new issues are linked into a stable version.
Most issues I have found (see https://www.wolfssl.com/docs/security-vulnerabilities) are located in the parsing process of the TLS messages client_hello and server_hello. These issues were buffer overflows or uninitialized memory. They could be fixed easily by simply adding a sanity check or a memory initialization. For the sake of completeness, it should also be mentioned that the wolfSSL TLS library source code includes about 521,655 lines of code (without comments and blanks). Hence, it is not easy to avoid issues without fuzzing.
What will be fuzzed in the future?
Currently I am testing the wolfSSL TLS library only, but wolfSSL provides further libraries, like wolfCrypt. These libraries interoperate and make use of each other. For example, the wolfSSL TLS library uses functions from the wolfCrypt library. So the other libraries must be tested, too. In the future, I will develop a new FAST framework for each of them. These new FAST frameworks will have the same features and approaches like the TLS-FAST framework. Over the time, new features will be added to these FAST frameworks.
My goal is to provide our customers a FAST framework as a testing service for their software products. This service detects all issues as quickly as possible.
If you have any questions or run into any issues, contact us at facts@wolfssl.com, or call us at +1 425 245 8247.
wolfSSL 4.6.0 Now Available
The Christmas release of wolfSSL is available! Get your version 4.6.0 copy by visiting the downloads page on wolfSSL’s website or checking out the release sections on our GitHub repository. A lot of engineering and exciting additions happened in this release. Some of our recent blogs have touched on the new features, this release had our Linux kernel module support, Apache httpd TLS 1.3 support, hardware acceleration additions for the NXP DCP (i.MX RT1060/1062) crypto co-processor, Silicon Labs hardware support and many more new features.
A full list of items in the release can be found in the bundled README.md but the following are a few of the notable changes:
- Linux Kernel Module! wolfSSL now enables Linux kernel module support with FIPS! Big news for Linux kernel module developers with crypto requirements! wolfCrypt and wolfSSL are now loadable as modules in the Linux kernel, providing the entire libwolfssl API natively to other kernel modules. For the first time on Linux, the entire TLS protocol stack can be loaded as a module, allowing fully kernel-resident TLS/DTLS endpoints with in-kernel handshaking. (
--enable-linuxkm,--enable-linuxkm-defaults,--with-linux-source). Read more in our blog. - New Apple A12Z Benchmarks! Build tests and updated instructions for use with Apple’s A12Z chipset. Read more and see benchmarks in our blog!
- wolfSSL Math Library! Expansion of wolfSSL Single Precision math implementation and addition of a new
--enable-sp-math-allbuild option — includes broader assembly support and is faster. - TLS 1.3 fixes and additions! A couple of the additions have been with Sniffer support and adding Apache httpd TLS 1.3 support. We are leading the way with TLS 1.3 sniffing, which is important to a small subset of users such as schools that wish to protect what young kids can view in computer labs.
- New Hardware Acceleration! Added support for NXP DCP (i.MX RT1060/1062) crypto co-processor and added Silicon Labs hardware acceleration using SL SE Manager.
FIPS certificate #2425 is being added to NIST sunset list: wolfSSL customers can achieve effortless transition to FIPS cert #3389
FIPS 140-2 requires the use of validated cryptography in the security systems implemented by federal agencies to protect sensitive information. The wolfCrypt Module is a comprehensive suite of FIPS Approved algorithms. All key sizes and modes have been implemented to allow flexibility and efficiency.
The National Institute of Standards and Technology (NIST) is sending FIPS cert #2425 into sunset June 2021. For customers who will be impacted, the wolfCrypt Cryptographic Module maintains its #3389 certificate and can be used in conjunction with the wolfSSL embedded SSL/TLS library for full TLS 1.3 client and server support. Upgrade your FIPS cert with wolfSSL to stay afloat and benefit from:
- Algorithm support for TLS 1.3!
- New algorithms such as AES (CBC, GCM, CTR, ECB), CVL, Hash DRBG, DSA, DHE, ECDSA (key generation, sign, verify), HMAC, RSA (key generation, sign, verify), SHA-3, SHA-2, SHA-1, and Triple-DES
- Hardware encryption support for NXP’s Cryptographic Assistance and Assurance Module (CAAM), NXP Memory-Mapped Cryptographic Acceleration Unit (mmCAU), Intel’s AES-NI, and more
- Support for secure elements and TPM’s
- Interoperability with wolfBoot, wolfSSH, and wolfTPM
- Integration support for third party libraries such as strongswan, nginx, python and more
Contact us to upgrade to FIPS cert #3389 at fips@wolfssl.com.
Additional Resources
Learn more about wolfSSL support for FIPS cert #3389: https://www.wolfssl.com/wolfcrypt-fips-certificate-3389-3/
For a list of supported Operating Environments for wolfCrypt FIPS, check our FIPS page: https://www.wolfssl.com/license/fips/
Our FIPS Story
wolfSSL is currently the leader in embedded FIPS certificates. We have a long history in FIPS starting with wolfCrypt FIPS 140-2 Level 1 Certificate #2425 as well as wolfCrypt v4 FIPS 140-2 Level 1 Certificate #3389. wolfSSL partners with FIPS experts KeyPair to bring you FIPS consulting services, and high assurance along each step of your FIPS certification process. Additionally, wolfSSL will be the first implementation of FIPS 140-3.
wolfSSL also provides support for a wolfCrypt FIPS Ready version of the library! wolfCrypt FIPS Ready is our FIPS enabled cryptography layer code included in the wolfSSL source tree that you can enable and build. You do not get a FIPS certificate, you are not FIPS approved, but you will be FIPS Ready. FIPS Ready means that you have included the FIPS code into your build and that you are operating according to the FIPS enforced best practices of default entry point, and power on self test.
wolfCrypt FIPS Ready can be downloaded from the wolfSSL download page located here: https://www.wolfssl.com/download/. More information on getting set up with wolfCrypt FIPS Ready can be found in our FIPS Ready User guide here: https://www.wolfssl.com/docs/fips-ready-user-guide/
If you have any questions or run into any issues, contact us at facts@wolfssl.com, or call us at +1 425 245 8247.
Weekly updates
Archives
- July 2025 (3)
- June 2025 (22)
- May 2025 (25)
- April 2025 (24)
- March 2025 (22)
- February 2025 (21)
- January 2025 (23)
- December 2024 (22)
- November 2024 (29)
- October 2024 (18)
- September 2024 (21)
- August 2024 (24)
- July 2024 (27)
- June 2024 (22)
- May 2024 (28)
- April 2024 (29)
- March 2024 (21)
- February 2024 (18)
- January 2024 (21)
- December 2023 (20)
- November 2023 (20)
- October 2023 (23)
- September 2023 (17)
- August 2023 (25)
- July 2023 (39)
- June 2023 (13)
- May 2023 (11)
- April 2023 (6)
- March 2023 (23)
- February 2023 (7)
- January 2023 (7)
- December 2022 (15)
- November 2022 (11)
- October 2022 (8)
- September 2022 (7)
- August 2022 (12)
- July 2022 (7)
- June 2022 (14)
- May 2022 (10)
- April 2022 (11)
- March 2022 (12)
- February 2022 (22)
- January 2022 (12)
- December 2021 (13)
- November 2021 (27)
- October 2021 (11)
- September 2021 (14)
- August 2021 (10)
- July 2021 (16)
- June 2021 (13)
- May 2021 (9)
- April 2021 (13)
- March 2021 (24)
- February 2021 (22)
- January 2021 (18)
- December 2020 (19)
- November 2020 (11)
- October 2020 (3)
- September 2020 (20)
- August 2020 (11)
- July 2020 (7)
- June 2020 (14)
- May 2020 (13)
- April 2020 (14)
- March 2020 (4)
- February 2020 (21)
- January 2020 (18)
- December 2019 (7)
- November 2019 (16)
- October 2019 (14)
- September 2019 (18)
- August 2019 (16)
- July 2019 (8)
- June 2019 (9)
- May 2019 (28)
- April 2019 (27)
- March 2019 (15)
- February 2019 (10)
- January 2019 (16)
- December 2018 (24)
- November 2018 (9)
- October 2018 (15)
- September 2018 (15)
- August 2018 (5)
- July 2018 (15)
- June 2018 (29)
- May 2018 (12)
- April 2018 (6)
- March 2018 (18)
- February 2018 (6)
- January 2018 (11)
- December 2017 (5)
- November 2017 (12)
- October 2017 (5)
- September 2017 (7)
- August 2017 (6)
- July 2017 (11)
- June 2017 (7)
- May 2017 (9)
- April 2017 (5)
- March 2017 (6)
- January 2017 (8)
- December 2016 (2)
- November 2016 (1)
- October 2016 (15)
- September 2016 (6)
- August 2016 (5)
- July 2016 (4)
- June 2016 (9)
- May 2016 (4)
- April 2016 (4)
- March 2016 (4)
- February 2016 (9)
- January 2016 (6)
- December 2015 (4)
- November 2015 (6)
- October 2015 (5)
- September 2015 (5)
- August 2015 (8)
- July 2015 (7)
- June 2015 (9)
- May 2015 (1)
- April 2015 (4)
- March 2015 (12)
- January 2015 (4)
- December 2014 (6)
- November 2014 (3)
- October 2014 (1)
- September 2014 (11)
- August 2014 (5)
- July 2014 (9)
- June 2014 (10)
- May 2014 (5)
- April 2014 (9)
- February 2014 (3)
- January 2014 (5)
- December 2013 (7)
- November 2013 (4)
- October 2013 (7)
- September 2013 (3)
- August 2013 (9)
- July 2013 (7)
- June 2013 (4)
- May 2013 (7)
- April 2013 (4)
- March 2013 (2)
- February 2013 (3)
- January 2013 (8)
- December 2012 (12)
- November 2012 (5)
- October 2012 (7)
- September 2012 (3)
- August 2012 (6)
- July 2012 (4)
- June 2012 (3)
- May 2012 (4)
- April 2012 (6)
- March 2012 (2)
- February 2012 (5)
- January 2012 (7)
- December 2011 (5)
- November 2011 (7)
- October 2011 (5)
- September 2011 (6)
- August 2011 (5)
- July 2011 (2)
- June 2011 (7)
- May 2011 (11)
- April 2011 (4)
- March 2011 (12)
- February 2011 (7)
- January 2011 (11)
- December 2010 (17)
- November 2010 (12)
- October 2010 (11)
- September 2010 (9)
- August 2010 (20)
- July 2010 (12)
- June 2010 (7)
- May 2010 (1)
- January 2010 (2)
- November 2009 (2)
- October 2009 (1)
- September 2009 (1)
- May 2009 (1)
- February 2009 (1)
- January 2009 (1)
- December 2008 (1)

